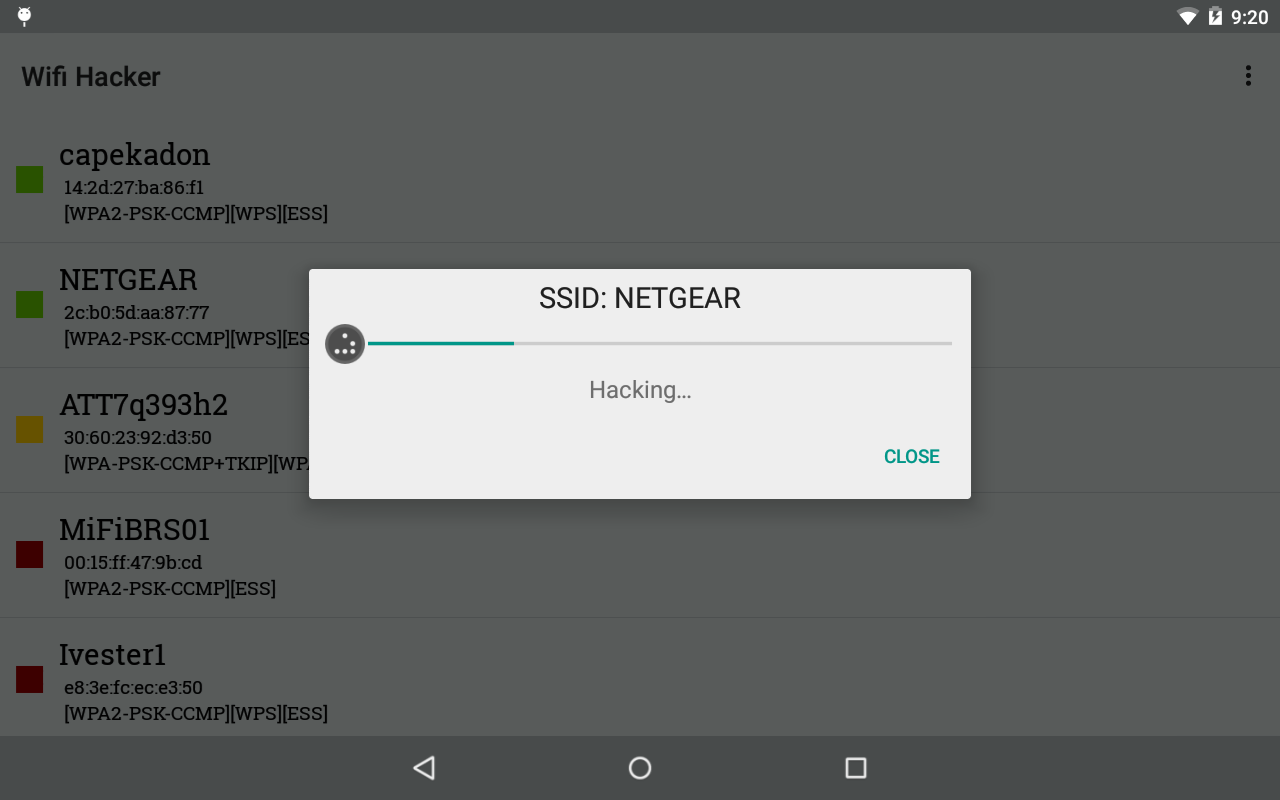
Is It Doable To Hack A WiFi Community Of WPA2-PSK Security?
 Since WiFi Alliance, ICASI, and many other institutions and router manufacturers had been knowledgeable in July about the problem, the primary security patches are already out there. WPA2, which requires testing and certification by the Wi-Fi Alliance, implements the mandatory elements of IEEE 802.11i. Particularly, it contains mandatory support for CCMP, an AES-based mostly encryption mode with sturdy safety. A “extreme” safety flaw with residence WiFi networks has been reported that probably places anyone utilizing a wireless router liable to being hacked. In this tutorial I’ll present to hack any WEP/WPA/WPA2 Wi-Fi connection using a bootable USB and beini.iso! 1. Write beini.iso on your USB by UNetbootin. 1. A USB pen drive. 2. After finishing restart your Computer and boot it out of your USB. 3. When you had been successful besides up then you should see one thing like this. Q. I cannot boot from the BT4 Disc? U key to open Utilities.
Since WiFi Alliance, ICASI, and many other institutions and router manufacturers had been knowledgeable in July about the problem, the primary security patches are already out there. WPA2, which requires testing and certification by the Wi-Fi Alliance, implements the mandatory elements of IEEE 802.11i. Particularly, it contains mandatory support for CCMP, an AES-based mostly encryption mode with sturdy safety. A “extreme” safety flaw with residence WiFi networks has been reported that probably places anyone utilizing a wireless router liable to being hacked. In this tutorial I’ll present to hack any WEP/WPA/WPA2 Wi-Fi connection using a bootable USB and beini.iso! 1. Write beini.iso on your USB by UNetbootin. 1. A USB pen drive. 2. After finishing restart your Computer and boot it out of your USB. 3. When you had been successful besides up then you should see one thing like this. Q. I cannot boot from the BT4 Disc? U key to open Utilities.
- After password cracked you may see it on terminal, as in picture below
- So it is better to go for reaver methodology if wps is obtainable
- 1 Download Passwords List/Wordlist for Kali Linux (2020 Version)
- Private and enterprise networks,
- Brand: TP-Hyperlink
- 3 * 11 WEP 16db no
5. Now Minipwep-gtk program will open. Now we are going to carry out ARP REPLAY Attack to the WiFi community to climb the info to the network at enormous price. Wi-Fi Security Historical past Acquired; Now What? A flaw in a feature added to Wi-Fi, called Wi-Fi Protected Setup, allows WPA and WPA2 security to be bypassed and effectively damaged in many situations. WiFi Hacker has the autodetect encryption function either then you don’t should know what encryption you need to crack. WPA and WPA2 security carried out with out utilizing the Wi-Fi Protected Setup characteristic are unaffected by the security vulnerability. On this submit we have been briefly describe you the right way to hack wifi in home windows and it was the best technique to hack wifi on windows Laptop through the use of JumpStart and Dumpper. The brand new technique to crack WPA/WPA2 enabled WiFi networks that allow attackers to entry Pre-shared Key hash that used to crack Passwords utilized by focused victims.
Steube factors out that he ignores in how many routers precisely this attack works, however he believes that the assault may very well be practical in opposition to all WiFi 802.Eleven i/p/q/r networks with roaming capabilities enabled. However Steube said it would work against all 802.11i/p/q/r networks with roaming capabilities enabled (most trendy routers). Now, as you possibly can see in the above image, wash reveals you all the WPS enabled Network. Watch this video tutorial if should not getting the above handbook process. Good luck and the dictionarys above are a must have. If you happen to twin-booted your system and/or using Ubuntu or Mint Linux, then you’re good to go. If you’re using laptop computer, then it doesn’t require any extra hardware. If your card is in a unique mode then the consumer card there is good probability that the shopper will not have the ability to accurately obtain your transmission. As you understand there are rather a lot of how to hack WiFi password.
 It takes time, a whole lot of it. WiFi Password Cracker could be very optimized tool which suggests it’s very fast and each operation takes only a couple of minutes. That means it works at hottest platforms: Windows, Mac, Linux, Android, iOS and Blackberry. In accordance with the researcher that found Krack, Mathy Vanhoef, it implies that an attacker would theoretically be capable to inject ransomware or different malware into otherwise benign web sites. Step 1 — An attacker can use a instrument, like hcxdumptool (v4.2.Zero or increased), to request the PMKID from the targeted entry point and dump the obtained body to a file. Within the ‘Networks’ tab, choose the community adapter you wish to use. In accordance with specialists in digital forensics from the Worldwide Institute of Cyber Safety, this assault is carried out within the Robust Security Network Information Factor (RSN IE), utilizing a single EAPOL framework after requesting it from the entry level.
It takes time, a whole lot of it. WiFi Password Cracker could be very optimized tool which suggests it’s very fast and each operation takes only a couple of minutes. That means it works at hottest platforms: Windows, Mac, Linux, Android, iOS and Blackberry. In accordance with the researcher that found Krack, Mathy Vanhoef, it implies that an attacker would theoretically be capable to inject ransomware or different malware into otherwise benign web sites. Step 1 — An attacker can use a instrument, like hcxdumptool (v4.2.Zero or increased), to request the PMKID from the targeted entry point and dump the obtained body to a file. Within the ‘Networks’ tab, choose the community adapter you wish to use. In accordance with specialists in digital forensics from the Worldwide Institute of Cyber Safety, this assault is carried out within the Robust Security Network Information Factor (RSN IE), utilizing a single EAPOL framework after requesting it from the entry level.