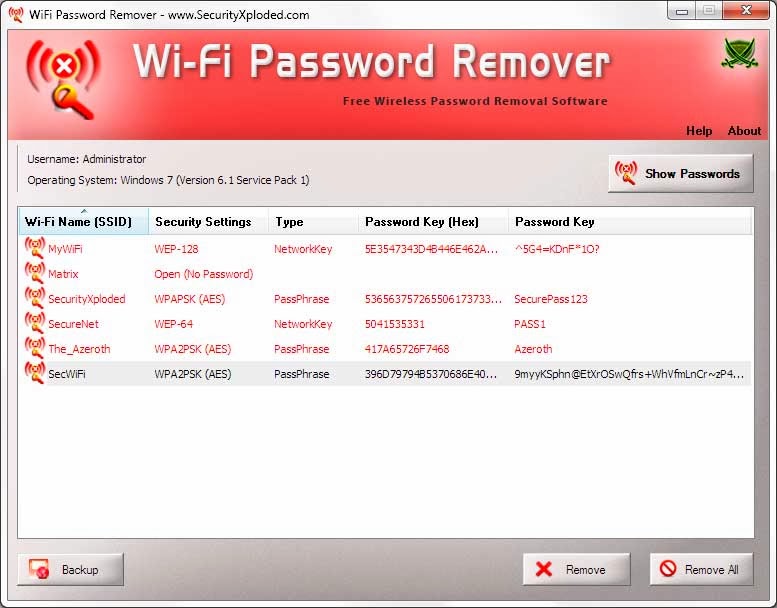
Hack Any WPA WPA2 WiFi Password
5. Now must scan wifi, so proceed typing, and at the moment that you must kind airodump-ng mon0 command and hit enter. When you kind it in, you’ll a bunch of passwords being tried against your hash file. Hashcat or cudaHashcat saves all recovered passwords in a file. Lastly, lets rename this file to wpa.lst. Lets do it again. Now that we’ve got our ESSID added to Pyrit database, lets go an import our Password Dictionary. Guarantee you may have permission before you attack an access level as it is a felony in many nations. We’ll use this data to trace the victim’s Access Level. It is not attainable for everyone each time to keep the system on and not use for personal work and the Hashcat builders understands this downside very properly. Thanks for studying. This process isn’t always attainable and generally cracking Wifi WPA/WPA2 passwords using Reaver-WPS is much simpler.
- Bssid in my case bssid is indicated with pink mark
- Type http://192.168.2.1 within the tackle bar and press Enter
- Good user interface
- To use the .cap in the hashcat first we’ll convert the file to the .hccapx file
- Beini.iso file. [Download it from right here]
- We can BruteForce assault it. 1. Amongst BruteForce, we can use crunch
Without his guide, a lot of this wouldn’t be doable. Obviously, this was much sooner than my Laptop computer. Nonetheless, with the consideration in thoughts, we should conlude the truth that we are not going to acheive much pace with python as will be completed by means of hashcat. You want not worry here I will information you the way are you able to hack WI-FI passwords either they’re protected with WPS or WPA or WPA2 in just 5 minutes easily. So we’re saving this file as newrockyou.txt title. Now, your wireless community adapter should have a name like “wlan0mon” and be in monitor mode. With a purpose to run wireless attacks utilizing airmon-ng it is important to change to watch mode as shown in Determine 1 under. Wi-Fi signals (shown beneath). Step 6: Once you finish the downloading course of, you can set up this app on your device to interrupt and use the Wi-Fi network that is available in the vary of your Android gadget.
That’s 14344392 passwords. So we made this file shorter which implies we are able to check extra AP’s in less time. That’s a whopping 9606665 passwords. That’s it. It would take few minutes to undergo the entire Database Desk to get the password if it existed within the Dictionary. Word: cowpatty will fail if your password/dictionary file is larger than 2GB. You’ll have to stick to airolib-ng regardless that that’s slower. Awesome, now now we have our ESSID added to Pyrit Database. Now we need to create ESSID in Pyrit Database. Lastly, if you’re feeling like, you may delete your essid and cleanup. We can crack using few completely different process. We now need to batch course of to create tables. Oh, and i just took this superior screenshot while Pyrit was doing the batch processing. However at least you don’t must batch course of this fashion. Now that we have our cowpatty output, let’s attempt to crack WPA2/PSK passphrase. You’ll need to assume they’ve WPS, after which transfer to next steps. To crack using cowpatty, you could export in cowpatty format and then begin the cracking process. If the network that you just wish to hack has an excellent sign and if your system is in good condition, then the hack completes in 5 – 18 Hours.
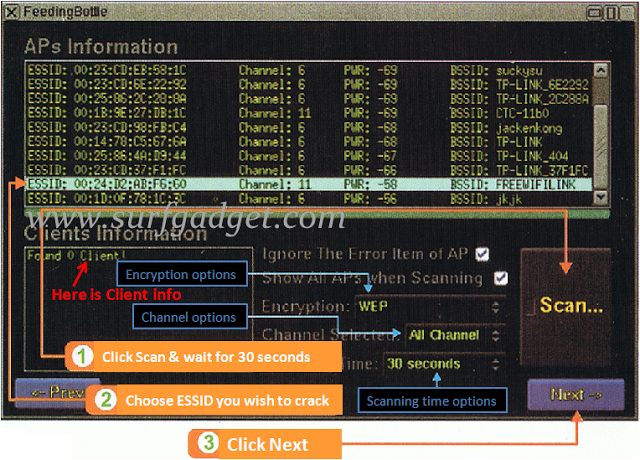 You might want to check that too. You’ll see the name of the wifi you want to hack. Interface identify is wlan0 and its at the moment working in Regular Mode. To call a couple of. WiFi Password Cracker is very optimized instrument which means it’s extremely fast and every operation takes only a couple of minutes. Your crack is in progress, and would take few hours to be cracked. 5 – 10 hours. 20 characters WPA2 password rely with our hardware and wireless card. 2. Kernel is the principle part of most laptop working techniques; it’s a bridge between functions and the precise information processing accomplished at the hardware degree. Edit this file to match your requirement, run Hashcat or cudaHashcat and let it rip. It is going to be in the identical listing you’ve ran Hashcat or cudaHashcat or oclHashcat. Let’s copy one in all finest dictionary file to root directory. As a result of WPA2 minimal password requirement is eight characters, let’s parse this file to filter out any passwords that is lower than 8 characters and more than 63 characters.
You might want to check that too. You’ll see the name of the wifi you want to hack. Interface identify is wlan0 and its at the moment working in Regular Mode. To call a couple of. WiFi Password Cracker is very optimized instrument which means it’s extremely fast and every operation takes only a couple of minutes. Your crack is in progress, and would take few hours to be cracked. 5 – 10 hours. 20 characters WPA2 password rely with our hardware and wireless card. 2. Kernel is the principle part of most laptop working techniques; it’s a bridge between functions and the precise information processing accomplished at the hardware degree. Edit this file to match your requirement, run Hashcat or cudaHashcat and let it rip. It is going to be in the identical listing you’ve ran Hashcat or cudaHashcat or oclHashcat. Let’s copy one in all finest dictionary file to root directory. As a result of WPA2 minimal password requirement is eight characters, let’s parse this file to filter out any passwords that is lower than 8 characters and more than 63 characters.