Methods To Crack WPA2 WPS WiFi Password
 13:04:20 Sending 64 directed DeAuth. It does not help packet injection, so deauth wasn’t working. This time I elevated the deauth frequency. 5W”, effectively not all the time, WPS hacking is around for quite some time. 14 phrases so use aircrack-ng for hacking . Enter the Aircrack-ng installation command. NO Installation Required/DVD Rom NOT Required,as long as your computer have Usb ports, Simply Plug and Play! Bootable(run from usb flash drive),Just insert Dwell Usb Flash Drive right into a usb port,set Laptop Boot Sequence/Boot Priority and restart laptop. 6 month warranty, if usb software malfunction within this period,just ship it back to me for reprogramming with your individual courier bills, i will ship it again to you below MY bills after i reprogram the usb drive. Now you may go back to your property as a result of the following steps could be carried out from wherever on the earth. Value RM350/USD120. Price can change anytime with out notice.
13:04:20 Sending 64 directed DeAuth. It does not help packet injection, so deauth wasn’t working. This time I elevated the deauth frequency. 5W”, effectively not all the time, WPS hacking is around for quite some time. 14 phrases so use aircrack-ng for hacking . Enter the Aircrack-ng installation command. NO Installation Required/DVD Rom NOT Required,as long as your computer have Usb ports, Simply Plug and Play! Bootable(run from usb flash drive),Just insert Dwell Usb Flash Drive right into a usb port,set Laptop Boot Sequence/Boot Priority and restart laptop. 6 month warranty, if usb software malfunction within this period,just ship it back to me for reprogramming with your individual courier bills, i will ship it again to you below MY bills after i reprogram the usb drive. Now you may go back to your property as a result of the following steps could be carried out from wherever on the earth. Value RM350/USD120. Price can change anytime with out notice.
And naturally, mon0 merely means the monitor interface, change it if yours is completely different. There is only a method that hackers get into your network, and that is with a Linux-primarily based OS, a wireless card capable of monitor mode, and aircrack-ng or similar. There are lots of hacking instruments that can be found on Internet that can hack a safe Wi-Fi network but this device is published by George Chatzisofroniou that automates the a number of Wi-Fi hacking techniques and make it slightly totally different from all others. There are hundreds of Home windows functions that claim they’ll hack WPA; don’t get them! At Present, we don’t know for which vendors or for what number of routers this hack will work, nevertheless many specialists imagine it’ll work towards all 802.11i/p/q/r networks with roaming functions enabled… basically most fashionable routers. You may see the name of the wifi you wish to hack. 2. Tips on how to hack any wifi utilizing wifite device.
- Finally, merge all text information into one using the below command
- W : password list (the one generated by Crunch)
- Apt set up hashcat
- In case you don’t see a monitor title, your Wi-Fi card doesn’t help monitoring
- Please follow beneath picture by follow the numbering and textual content in crimson coloration
The RSN IE is the optional subject that acts because the container to the Pairwise Master Key identifier (PMKID) which is created by the router when a person tries to hook up with the WiFi community. Test your router safety strategies supported which is in its configuration page. As shortly because the victim requests a web page from the web, wifiphisher can reply with a smart pretend page that asks for credentials or serves malware. This module will be present in other audit applications, as wifi was or wifis lax. Jika secret word WiFi sudah dapat dan terlihat, maka silahkan anda gunakan watchword tersebut untuk mengakses jaringan Wifi yang ada. Demikianlah postingan mengenai cara membobol secret key WiFi dengan pengamanan WpA/WPA2-PSK by means of HP android ataupun bisa juga dengan workstation. Now on the subsequent display screen, in the terminal window you may see all of the close by available wifi networks. To download it to our Desktop, sort the following commands right into a terminal window. Enter the following command to change the title, making sure to exchange “name” with whatever you need to call the file: mv ./-01.cap name.cap- In case your “.cap” file isn’t named “-01.cap”, exchange “-01.cap” with no matter your “.cap” file’s identify is.
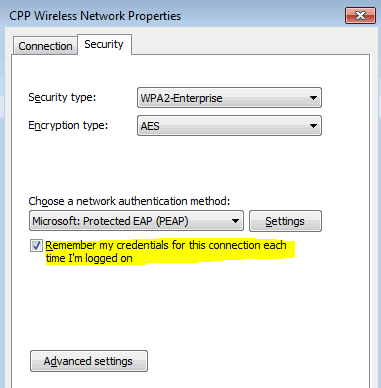
Type the following command into your terminal window, modifying the password listing to match where you saved yours. These are the mostly used encryption methods for making certain password safety and stopping unauthorized utilization of the Web or Wi-Fi connection sources. Older methods require the capture of the full authentication handshake wheras this new exploit solely requires a single body which may be simply obtained from the Entry Level. Kind this point forward, you do not should be wherever close to the wireless community. The PMK performs an necessary half within the 4-means handshake that’s used to authenticate both the consumer and router recognized Pre-Shared Key (PSK) or the wireless password of the network. 3. Proper-click on the identify of your wireless community, and then click on Standing. The tool also managed to repeatedly cause the router to stop responding to different computers on the network, primarily creating a denial of service DoS assault.