A New WiFi Hacking Methodology For WPA/WPA2
So, you can kill them utilizing the syntax: kill PID if you understand these processes should not important for you in the meanwhile. Kill any processes that return errors. How do hackers and crackers break WiFi encryption for WEP WPA WPA2 WPS Keys in an easy way with software? One beneficial device that may protect your router from hackers is a firewall. The United States Computer Emergency Readiness Staff (US-CERT) has issued an alert about Russian state-supported hackers carrying out assaults in opposition to a large number of dwelling routers within the U.S. Some individuals simply await a pc to attach. Alright, now, your computer has many network adapters, so to scan one, that you must know its title. You may watch this video to know how one can hack wifi utilizing kali linux using reaver method. It was one of many fantasies of mine to know such methodology which does exactly what we gonna do right here in this text.
- Permutation assault
- Disable the monitor mod
- Sort: ./configure
- Brute-Force assault
- Select the wifi ssid you want to crack
- Flip In your monitor interface by typing the beneath command
- Wireless Adapter
- Good user interface
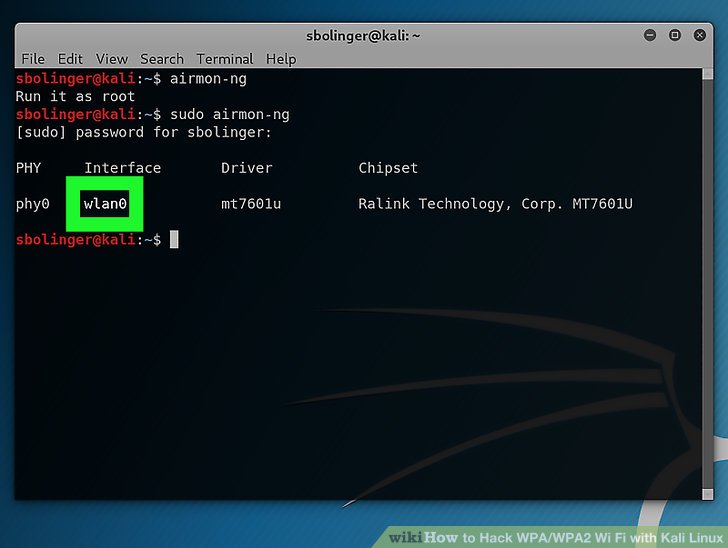
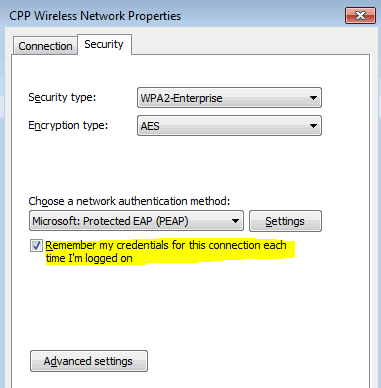
Understand the commands used and applies them to one of your individual networks. The Krack WPA2 attack can be used against all modern protected WiFi networks and can be used to inject other types of malware, similar to ransomware, into web sites by manipulating information. Many entry level they’ve a Wifi Protected Setup enabled by default (even after we exhausting reset the entry point). Passcovery Suite runs even faster on AMD/NVIDIA graphics playing cards. Passcovery Suite is the common password restoration instrument. If you’re very close to the network, you would try a WiFi spoofing device like wifi-honey, to attempt to fool the device into considering that you’re the router. This device gathers data from the wireless packets within the air. After that, you’ll be able to see all available network (rely on your wireless card vary). By no means thoughts I see your second post now. As a alternative, most wireless entry factors now use Wi-Fi Protected Entry II with a pre-shared key for wireless safety, often known as WPA2-PSK. When Wi-Fi was first developed within the late nineteen nineties, Wired Equivalent Privacy was created to offer wireless communications confidentiality.
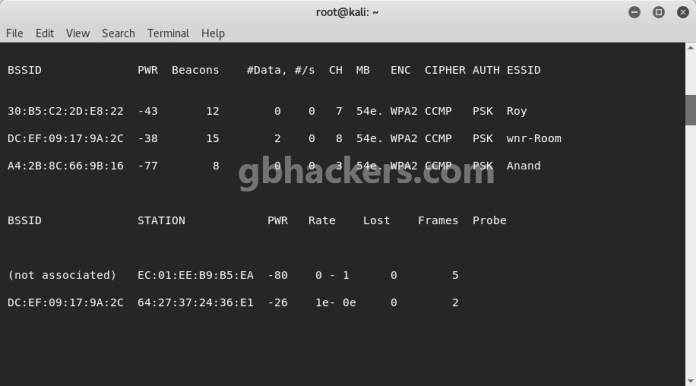
Networks Basics: in this section you’ll study how networks work, how gadgets talk with one another and how the data is transferred in a wireless networks. Replace “MAC” with the MAC handle you found in the last part. When you see the “WPA handshake:” tag and the deal with subsequent to it, you’ll be able to proceed with hacking your community. You will see the name of the wifi you need to hack. Right here, -c 1 indicates channel number which is 1, -w bell is to put in writing information in file “bell”, -bssid 64:0F:28:6B:A9:B1 is MAC tackle for my selected WiFi entry level and mon0 is monitor interface that was created above. Write output to a file. This may begin a dump on the selected AP (00:25:9C:97:4F:48), on the selected channel (-c 9) and save the the hash in a file named cowcrack. Now that we’ve got the hash of the password, we will use it with cowpatty and our wordlist to crack the hash. We are able to use these recordsdata to feed hashcat. It is extremely recommended to not use this methodology in any of the illegal activities. To view the network password on a Mac, select a way to open the Keychain Access application, and then access Passwords.
With our wireless network adapter in monitor mode as “wlan1mon,” we’ll execute the next command to start the attack. The –deauth tells aireplay to launch a deauth assault. You may additionally need so as to add –ignore-damaging-one if aireplay demands it. C on the airodump-ng terminal to stop monitoring the community, however don’t close it but just incase you want some of the data later. WEP Cracking: Now that you’ve got gathered information about all of the networks around you, and found your goal, you will discover ways to crack the key that the target uses. Airodump with now monitor solely the goal community, allowing us to capture more specific information about it. The passphrase is a phrase or a sentence, without or with out areas, normally greater than 20 characters long. I fyou are successfully on hacking some Wi-Fi networkds then you can do extra then this. On this tutorial from our Wi-Fi Hacking series, we’ll look at utilizing aircrack-ngand a dictionary attack on the encrypted password after grabbing it within the 4-way handshake. Now when you look on the airodump-ng screen, you may see that at the highest proper it says WPA handshake captured .