Cracking The Passwords Of Some WPA2 Wi-Fi Networks Just Received Simpler • The Register
Once we have a look at beforehand available WiFi Hacking attacks for WiFi Hackers, we want to sit down again and wait till the target person logged in later we can crack the key by capturing the four-means handshake. Wikipedia, for example, lists a collection of safety flaws which were recognized since WPA2 was launched in September 2004. Essentially the most high profile, maybe, was the key Reinstallation Assault, or KRACK attack, recognized last 12 months. So Now we should Enter the Final and Ultimate Commands To Hack The WiFi Password And Now Hit Enter. Now you’ll get Handshake Packets On the highest Proper Nook Side Of the Terminal as we have now highlighted that in below Image. In accordance with the researcher, the previously recognized WiFi hacking strategies require attackers to wait for somebody to log into a community and capture a full 4-manner authentication handshake of EAPOL, which is a community port authentication protocol.
- This tool has a person-friendly interface
- YOU Will need to have Put in Kali Linux
- Elcomsoft Wireless Security Auditor (Obtain)
- Now we get the hccapx file
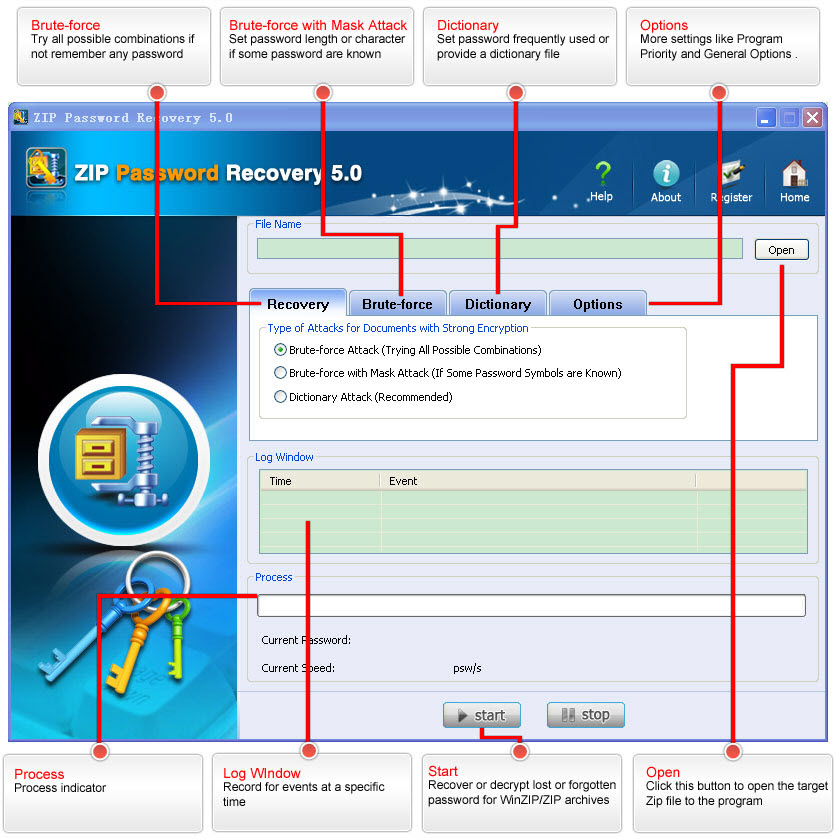
- It consumes less time than Brute Drive Assault Or Dictionary Attack
- Click on the Save option and select your file format Commview Seize Files (*.ncf)
- 0 Deauth Assault
“The most important difference from present assaults is that in this attack, capture of a full EAPOL 4-manner handshake is not required. With this characteristic, it permits users to put Web-of-Issues appliances on a separate network, shielding your central computer systems and other personal devices from attacks. With this digital zoning of your community, you’ll be able to nonetheless enable all your smart appliances and hubs to speak with each other while preserving your fundamental computing devices protected in the event of an Internet-Of-Things attack. Please ensure you set up a robust and tremendous-safe password on your visitor community, as nicely. Use a password generator to make something sturdy, aiming for thirteen characters or extra. Otherwise, for now, the neatest thing you are able to do is make sure that that you’ve a powerful password in your community. In case you are required to enter a password to connect to your Wi-Fi, you have already got some encryption enabled in your router. Considered one of the good issues with WPA3 is that succesful devices are backwards-appropriate with older ones that do not help it, because of the WPA3-Transition mode. In the event you supply -h/–help argument with a valid mode, you’re going to get all of the out there choices for that mode.
However this system wastes resources and we must live perpetually to get the outcomes. However I don’t want to get lost in clarification about Amazon AMI. On this case, we pay Amazon for the hours that we use, we can’t lose time! The timing is still too lengthy, and we can’t wait endlessly. If there is not any firmware update or your router updates however you are still stuck with WPA or WEP, it is time to purchase a brand new router. WPA, like its predecessor WEP, has been shown via both proof-of-concept and applied public demonstrations to be susceptible to intrusion. Unfortunately, this quest of ours has been invariabily one of those which normally have lesser outcomes and we usually find yourself with something like Rogue AP. Simply add -session at the top of the command you wish to run followed by the session name. Once a password has been imported, we are able to run a batch command to create a DB.
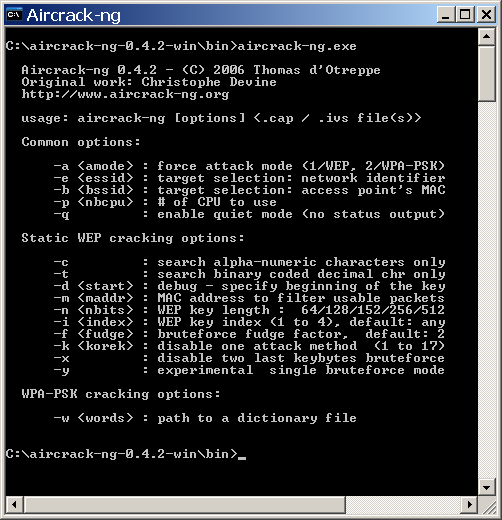
Aircrack-ng is used to run the brute power password cracking attack. All we have to do is locate a WiFi hotspot nearby our home or public place and simply use the software program for looking out and retrieving its password. Yes, potentially… we’re nonetheless at an excessive amount of time to crack with just one AMI, we’d like many AMI machines to attach all collectively and create a distributed service. So first, earlier than we purchase AMI services, we’d like to arrange a prepared package deal with own tools inside. Guest networks are meant for visitors to your private home who may need a Wi-Fi web connection, however you don’t want them gaining access to the shared recordsdata and units within your network. Nowadays, nearly all routers use a secure channel by default that relies onWi-Fi Protected Access II (WPA2). Newer routers do this segmentation routinely. Different researchers have already began making an attempt out the attack, so an inventory of weak routers seems to be in the making.
 Due to the MiTM attack, it is feasible to extract an encrypted password. The length and variation of your password is becoming more and more essential. Now we will still hack into, doubtlessly, any WPA2 passphrase size. Now we’re not sure about which vendors this wifi hack technique will work. We’re diving you particulars about three helpful software that will train you easy methods to hack WiFi password Crack Wireless. On the lookout for the right way to hack WiFi password OR WiFi hacking software? In different phrases there will not be lots of people around me that will try to steal or crack my password. Let’s see what occurs after we attempt to create a phrase checklist with Crunch. If we start a benchmark test on Linux AMI we will see soon the distinction. The replica is sort of precisely the same, the only difference being it is not WPA2 protected. With the name of the password checklist additionally being inputted into the command (-w iphonepasslist proven in blue font). What number of charter does your space embrace password has? This manner you won’t take up area with useless information. Subsequently, if you would like a simple means out without indulging within the otherwise unethical act of hacking/cracking wireless network passwords then merely convert your Computer right into a hotspot wherever you are.
Due to the MiTM attack, it is feasible to extract an encrypted password. The length and variation of your password is becoming more and more essential. Now we will still hack into, doubtlessly, any WPA2 passphrase size. Now we’re not sure about which vendors this wifi hack technique will work. We’re diving you particulars about three helpful software that will train you easy methods to hack WiFi password Crack Wireless. On the lookout for the right way to hack WiFi password OR WiFi hacking software? In different phrases there will not be lots of people around me that will try to steal or crack my password. Let’s see what occurs after we attempt to create a phrase checklist with Crunch. If we start a benchmark test on Linux AMI we will see soon the distinction. The replica is sort of precisely the same, the only difference being it is not WPA2 protected. With the name of the password checklist additionally being inputted into the command (-w iphonepasslist proven in blue font). What number of charter does your space embrace password has? This manner you won’t take up area with useless information. Subsequently, if you would like a simple means out without indulging within the otherwise unethical act of hacking/cracking wireless network passwords then merely convert your Computer right into a hotspot wherever you are.