5 Steps Wifi Hacking – Cracking WPA2 Password
It would show you the road containing “WPA” and corresponding code. One of many most vital changes between WPA and WPA2 is the mandatory use of AES algorithms and the introduction of CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) as a replacement for TKIP. However, it differs from other WiFi hacking methods; this attack does not require capturing a four-method LAN Extensible Authentication Protocol (EAPOL) authentication handshake. That is where hcxtools differs from Besside-ng, in that a conversion step is required so as to prepare the file for Hashcat to make use of. Merely sort the following to put in the newest model of Hashcat. Its a password for connecting to wifi community, wpa2 is the kind of network safety that the wifi network is using also comes as wep and wpa but wpa2 is most secure. First, be certain your laptop is connected (both wired or wirelessly) to your router, open a web browser and sort in the router’s IP tackle. You’ll have a lot of encryption options: if you continue to have an older router, you need to pick out one which begins with “WPA2.” In case your router just isn’t WPA3 compatible, then “WPA2-PSK AES” is your best possibility proper now.
 If you are looking for a new router, search for one that supports the most recent safety commonplace called WPA3. Never select Open (no security), or whether it is utilizing WEP, change the safety setting instantly. Routers with this functionality have open source router software support (comparable to DD-WRT), and they are often configured to make use of services like OpenVPN. An open network will make it simple for somebody to steal your Wi-Fi, and the older WEP security is easily hacked. If the one encryption options your router has are WEP or WPA, tell your router to test for a firmware update. WEP was ratified as a Wi-Fi safety normal in September of 1999. The primary variations of WEP weren’t significantly robust, even for the time they had been launched, because U.S. Amazon Net Companies gives ongoing security and maintenance updates to all cases working Amazon Linux AMIs. Replace your router: Update your router as quickly as updates are available. Before you start, make sure you will get into your router’s administration console; that is where you handle your router’s settings, including password administration to firmware updates.
If you are looking for a new router, search for one that supports the most recent safety commonplace called WPA3. Never select Open (no security), or whether it is utilizing WEP, change the safety setting instantly. Routers with this functionality have open source router software support (comparable to DD-WRT), and they are often configured to make use of services like OpenVPN. An open network will make it simple for somebody to steal your Wi-Fi, and the older WEP security is easily hacked. If the one encryption options your router has are WEP or WPA, tell your router to test for a firmware update. WEP was ratified as a Wi-Fi safety normal in September of 1999. The primary variations of WEP weren’t significantly robust, even for the time they had been launched, because U.S. Amazon Net Companies gives ongoing security and maintenance updates to all cases working Amazon Linux AMIs. Replace your router: Update your router as quickly as updates are available. Before you start, make sure you will get into your router’s administration console; that is where you handle your router’s settings, including password administration to firmware updates.
Sign in to the router’s log-in page. The IP deal with is a set of numbers, and the default depends in your router’s manufacturer. If you’re don’t know your router’s IP handle or password, it’s on the internet. We don’t know the maximum value of our phrase record, so we will ask it to Pyrit. In fact I know all my neighbors. Some routers are inherently flawed and may never be fixed. The algorithms are used to generate the default WPA2 password. Adding special characters or punctuation into your password is an efficient methodology of generating a more secure password as this drastically will increase the number of permutations possible and reduces the chance of a dictionary attack. We’ll need to start from there, examine the variety of characters, on this case 5, and restart Crunch with the new command. To amplify it, start a new VM and continue where we left off.
- Hcxtools v4.2.0 or higher
- 1 me 1 WPA2 44db wps client
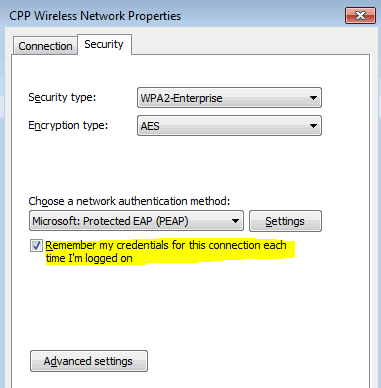
- Double-click the wireless community title, then select the Show password examine box
- Description: Kali GNU/Linux 2.Zero
3. Click WiFi Setting from the left menu. Most assault methods towards WiFi networks involve ready until a consumer connects and capturing data from the ‘handshake’ procedure between user and community, earlier than conducting a brute-power assault for the password. Whereas the new attack towards Wi-Fi passwords makes it simpler for hackers to attempt an assault on a goal, the same methods that had been effective against previous types of WPA cracking stay efficient. The large distinction to previous methods is apparently that cybercriminals do not must capture a full 4-method handshake. So first, earlier than we buy AMI companies, we want to arrange a ready package deal with personal tools inside. After all, to ensure that this device to work, there needs to be someone else related to the network first, so watch the airodump-ng and wait for a client to indicate up. The new attack as an alternative is carried out on the RSN IE, the Robust Safety Network Info Element, of a single EAPOL body.