WPA2 Or WPA3 Finest; By No Means Use Simply Hackable WEP
As is the case with all security standards, increasing pc power and exposed vulnerabilities have rendered older Wi-Fi requirements at risk. DropBox suffered an analogous case like this in 2012 as one of their employees used the identical password for LinkedIn as they used for his or her corporate DropBox account. He additionally labored for safety corporations like Kaspersky Lab. Within the last 24 hours, the media has broadly lined the WiFi WPA2 security hack. The shortest password allowed with WPA2 is 8 characters lengthy. Thus the only solution to get rid of this chance is to blacklist the leaked passwords at password creation. A dictionary that is used in such attacks may be a collection of beforehand collected key phrases or leaked passwords. The phrase lists are pushed out from knowledge breaches like each time an organization gets hacked then the stolen data is either offered out on the darkish net or leaked on a certain webpage like Pastebin.
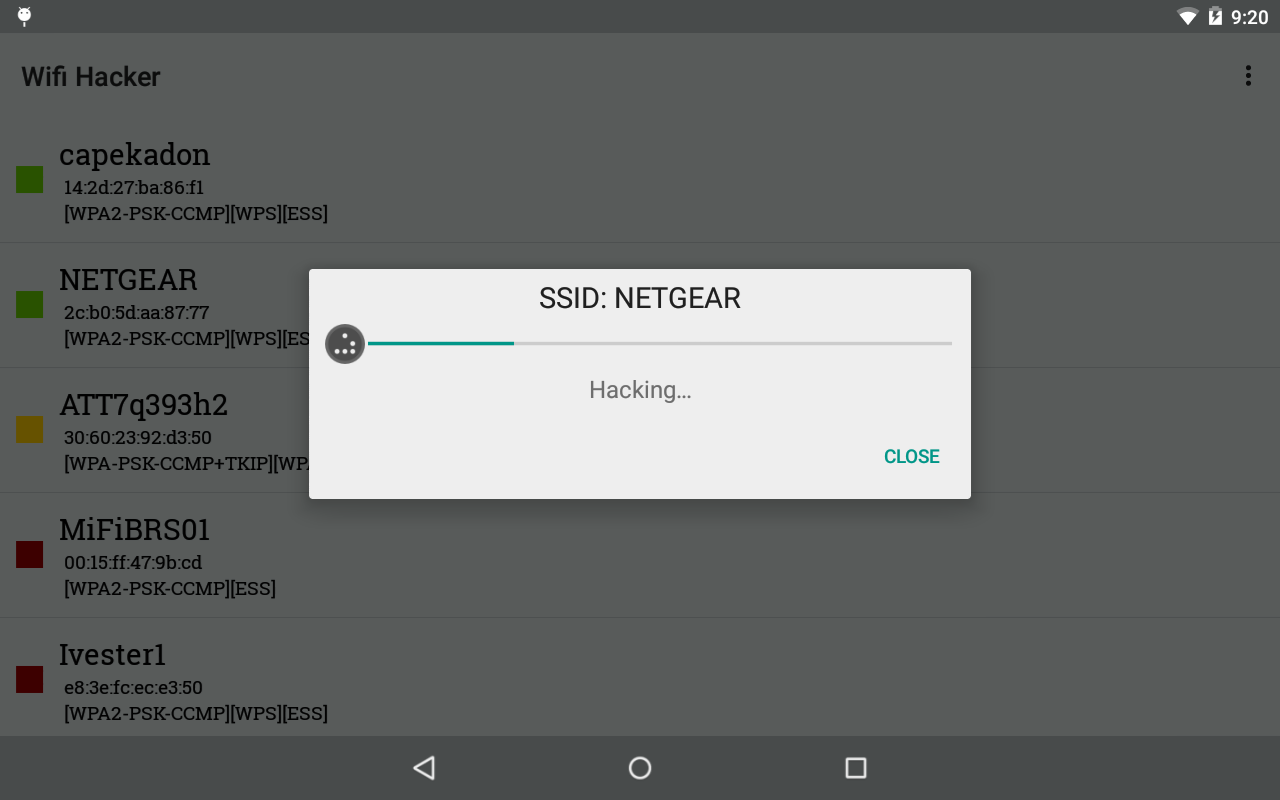
 Now, on this case, a simple adapter like WN722N would be enough the produce the PMKID. If none show up after a lengthy wait, then the community might be empty right now, or you’re to far away from the network. 5. Click the safety tab, and then choose the Present characters verify box to see the wireless community safety key (your password). The new WiFi hacking method permits to crack WPA/WPA2 wireless network protocols with Pairwise Grasp Key Identifier (PMKID)-based mostly roaming options enabled. They is perhaps labeled differently, but look for options below your router’s advanced settings like NAT filtering, port forwarding, port filtering and companies blocking. This specific method specifically works towards WPA and WPA2-secured Wi-Fi networks with PMKID-primarily based roaming options enabled, and it can be used to get well the PSK (Pre-Shared Key) login passwords. The safety flaw was discovered, by accident, by safety researcher Jens Steube whereas conducting checks on the forthcoming WPA3 security protocol; specifically, on differences between WPA2’s Pre-Shared Key trade course of and WPA3’s Simultaneous Authentication of Equals, which is able to exchange it.
Now, on this case, a simple adapter like WN722N would be enough the produce the PMKID. If none show up after a lengthy wait, then the community might be empty right now, or you’re to far away from the network. 5. Click the safety tab, and then choose the Present characters verify box to see the wireless community safety key (your password). The new WiFi hacking method permits to crack WPA/WPA2 wireless network protocols with Pairwise Grasp Key Identifier (PMKID)-based mostly roaming options enabled. They is perhaps labeled differently, but look for options below your router’s advanced settings like NAT filtering, port forwarding, port filtering and companies blocking. This specific method specifically works towards WPA and WPA2-secured Wi-Fi networks with PMKID-primarily based roaming options enabled, and it can be used to get well the PSK (Pre-Shared Key) login passwords. The safety flaw was discovered, by accident, by safety researcher Jens Steube whereas conducting checks on the forthcoming WPA3 security protocol; specifically, on differences between WPA2’s Pre-Shared Key trade course of and WPA3’s Simultaneous Authentication of Equals, which is able to exchange it.
- A word checklist
- Hybrid assault
- Check in to the router’s log-in page
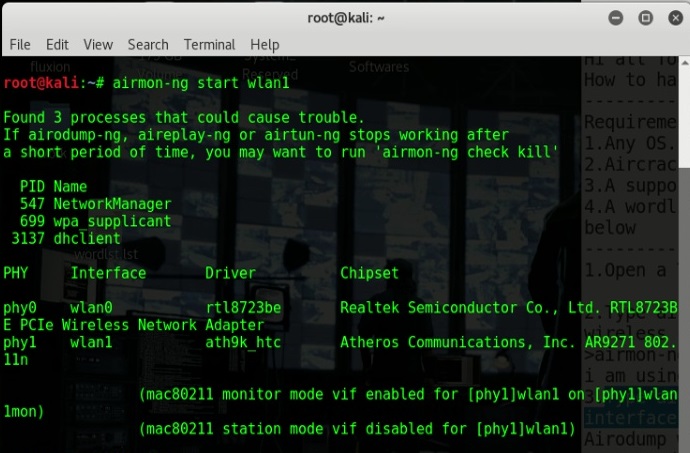
- Remember to change “mon0” with whatever your interface identify was
- Easy to used not need particular coaching
- Performing Sniffing on Customers Mode , which suggests you can monitor all users’ movements
- Description: Kali GNU/Linux 2.0
It also replaces the Pre-Shared Key alternate process with Simultaneous Authentication of Equals and will, subsequently, avoid the insecurity Steube uncovered in WPA2. In response to Steube, this assault might be a lot more durable to drag off against WPA3 due to its modern key institution protocol known as Simultaneous Authentication of Equals (SAE). The assault to compromise the WPA/WPA2 enabled WiFi networks was by chance found by Steube while he was analyzing the newly-launched WPA3 security commonplace. So sure, it’s going to reduce your time to hack WPA or WPA2 WiFi networks password a number of folds. Cracking the password would possibly take a long time relying on the dimensions of the wordlist. To avoid confusion together with your major network, arrange your visitor community with a special network identify (SSID) and password. The IP tackle is a set of numbers, and the default relies upon on your router’s producer. To test in case your router’s firewall and your ports are secure, you can use a web-based device for a quick test. Find your community or the community that you have permission to penetration take a look at.
Anyhow, after all, do not try any of the knowledge below in case you don’t have correct authorization by the network admin to take action. There are various components that play into it and one is, in fact, the router. The vast majority of individuals out there do not know much about community safety, if in any respect, however thankfully there are gifted groups and people on the market who are on fixed lookout for flaws and vulnerabilities. The community password could be weak and really straightforward to break, however with out a machine related to briefly kick off, there is no alternative to seize a handshake, thus no likelihood to try cracking it. With assist of WiFi password revealer, you can retailer all of your WiFi community passwords and it will show you all at any time when it’s worthwhile to check. You may hearken to the Kim Komando Present on your phone, tablet or pc. First, ensure that your laptop is related (either wired or wirelessly) to your router, open an internet browser and sort in the router’s IP handle. As soon as the file has downloaded, attach a flash drive to your pc and drag the downloaded Kali Linux ISO file onto it. We’ve got additionally shared some helpful tips on how to remain protected from dictionary attacks and how to use wordlists in Kali Linux.
With this function, it permits users to put Web-of-Things appliances on a separate network, shielding your central computers and different private gadgets from assaults. Such assaults may be harmful to your online business. You may clean up wordlists by using bash one-liner. The wordlists that you may get online together with the ones that we are going to share for you listed here are a set of common and unusual passwords that had been utilized by actual individuals no less than once. We are sharing with you Passwords listing and Wordlists for Kali Linux to obtain. To hack WPA/WPA2 Wi Fi with Kali Linux, begin by downloading the Kali Linux installation image by going to the Kali website and clicking HTTP. To begin the WIFI PASSWORD (WEP-WPA-WPA2), you’ll have to tap on its welcome screen once. Hey, Guys As we speak we are going to Discuss The way to HACK WiFi WPA2 Password? Recently, this idea emerged of cracking WPA2 in cloud servers.