Hacking WPA/WPA2 Wi-Fi Password With Kali Linux Using Aircrack-ng Step-by-step
Now, we’ll use airodump-ng to seize the packets in the air. So, Simply have a brief look on the steps and methods & instruments that we gonna use right here. Search for a set of sixteen alphanumeric characters. You need to attempt booting Kali utilizing Reside USB (just have a look at the first a part of this tutorial), or buy an external card. If I had been you, I might grab a Stay CD of Kali since BT has advanced into Kali. We’re sharing with you Passwords listing and Wordlists for Kali Linux to download. When you simply cannot find the password no matter what number of wordlists you try, then it appears your penetration take a look at has failed, and the network is at least safe from primary brute-pressure attacks. Subsequent, we’d like to begin a seize file where the hashed password will likely be stored when we capture the 4-method handshake. You’ll need to make use of a flash drive with not less than 4 gigabytes of space for this course of. In this tutorial, we’ll use the piece of software program developed by wireless safety researcher Joshua Wright (typically stylized as coWPAtty).
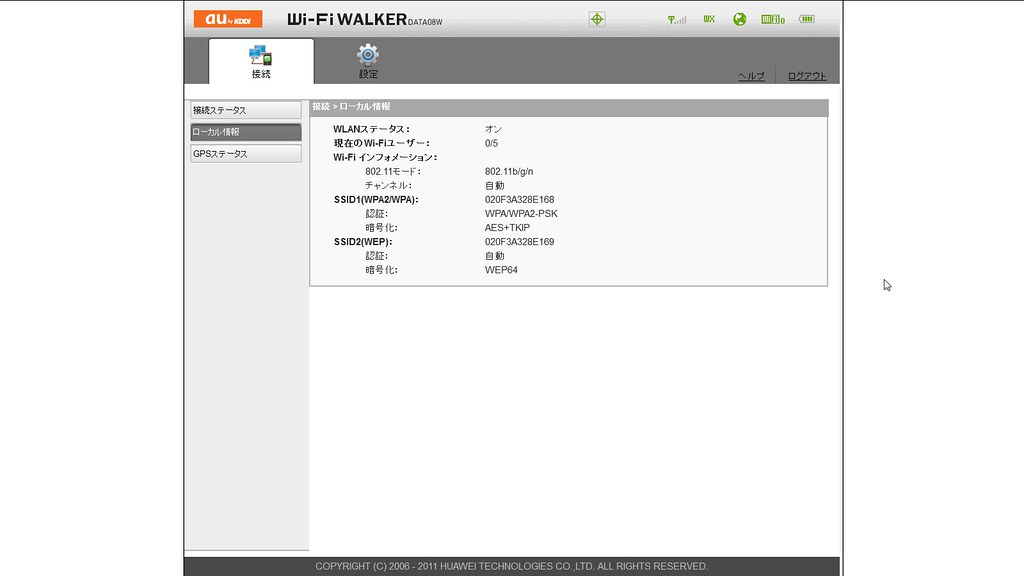
On this tutorial from our Wi-Fi Hacking sequence, we’ll look at utilizing aircrack-ngand a dictionary assault on the encrypted password after grabbing it within the 4-manner handshake. Now when someone connects to the AP, we’ll capture the hash and airdump-ng will present us it has been captured within the upper proper-hand nook. As you can see in the screenshot above, cowpatty is producing a hash of every word on our wordlist with the SSID as a seed and comparing it to the captured hash. Cowpatty now supports utilizing a pre-computed hash file reasonably than a plain-textual content word file, making the cracking of the WPA2-PSK password 1000x quicker! When you neglect the password to your access point, Wi-Fi Protected Setup, higher known simply as WPS, allows you to connect to the network utilizing an 8-digit quantity printed on the bottom of the router. I simply installed a wi-fi network extender and abruptly my wife’s 2010 MacBook Professional (Sierra) is asking for a WPA2 password to access one in all our wi-fi networks. Treat it like a installed version since it should remember everything you do on subsequent boot up. In case you are on the Pen-take a look at path you need a Pen-test OS Like Backtrack.
In some distribution, it is named something totally different like wlXXXX. However the researcher offers it improper by exploiting the vulnerability and named it as Dragonblood. Sadly, quite a lot of issues can go fallacious. The file could be reused in quite a few different instances together with the famous hashcat tool. 4. From the step three above, we can discover entry point with encryption algorithm WPA2 and notice the AP channel number. As soon as the PMKID is captured, the following step is to load the hash into Hashcat and attempt to crack the password. Now that we have the hash of the password, we will use it with cowpatty and our wordlist to crack the hash. Cowpatty should take the password checklist you present and compute the hash with the SSID for every phrase. Hashcat picks up phrases one by one and check them to the each password possible by the Mask defined. The place does one find the WPA2 password for Mac OS 10.12 Sierra? This means that the same password on different SSIDs will generate different hashes.
- It pings the DNS till the right combination of the password is found
- Then decompress (if relevant)gunzip *.gz
- We’ll use locate cap2hccapx command to search out the place the this converter is located
- L customizable settings (timeouts, packets/sec, and so on)
172,000 dictionary file and the 1,000 most popular SSIDs. This should produce a PCAPNG file containing the knowledge we have to attempt a brute-forcing assault, but we are going to need to transform it right into a format Hashcat can perceive. In case your community would not even support the strong security factor containing the PMKID, this assault has no likelihood of success. In case you don’t see a monitor name, your Wi-Fi card doesn’t support monitoring. We don’t create a manufacturing machine but solely a template for saving time and performing multi-creations. VM creation, word creation, and importing to Pyrit database are accomplished just one time. Other people send DEAUTH packets to kick them off the wifi, after which they routinely connect again, at which time you’ll capture the handshake. Up to now couple years, cloud computing has turn into the most widespread norm amongst the computer industries and now persons are utilizing it to mine websites and information. And, If you are a type of curious individuals – who wish to unleash this secret to yourself.
Guest networks are meant for visitors to your home who might need a Wi-Fi web connection, but you don’t need them gaining entry to the shared information and gadgets within your community. It makes use of the PMKID key to determine a connection between shopper and an access level. When a client authenticates to the access level (AP), the shopper and the AP undergo a 4-step process to authenticate the consumer to the AP. It’s essential to entry your routers admin pages and discover the wireless tab and look it up. Now a new popup will appear titled as “Wi-Fi Status” there in the overall tab click on the Wireless properties option. WEP Cracking: Now that you have gathered details about all of the networks round you, and located your goal, you’ll learn to crack the important thing that the target uses. Now whenever you look on the airodump-ng screen, you’ll see that at the highest proper it says WPA handshake captured . In my case airodump-ng says fixed channel mon0: -1 so this was required. You will also find out about basic terminology, what’s a channel ?