The Distinction Between WEP, WPA, And WPA2 Wi-Fi Passwords
To be able to crack a WPA password, .The way to crack WPA/WPA2 password with the help of android telephone? WPA – WiFi Protected Entry (WPA) is improved and more secured safety protocol which arrived with a lot of improvements in encryption and authentication methods of WEP. A “severe” security flaw with house WiFi networks has been reported that potentially puts anyone using a wireless router susceptible to being hacked. The PMK is a part of the traditional 4-manner handshake that’s used to verify that each the router and consumer know the Pre-Shared Key (PSK), or wireless password, of the network. There are several apps that assist the user hack a Wi-Fi network password with 100% accuracy. If you’re looking for to hack a Wi-Fi Password or Wi-Fi hacking software program then, we are right here to assist you thru this easy guide. With the assistance of contemporary routers, it has change into fairly simple for hackers to crack a Wi-Fi password. Within the outdated and former Wi-Fi hacking strategies, the hackers want to attend for someone until they log into the community.
The primary goal of this system is to protect any native or residence network with a password in order that one or more networks entry factors can not attack the network and get started using your Wi-Fi without spending a dime. Wi-Fi Protected Setup permits typical customers who possess little understanding of conventional Wi-Fi configuration and safety settings to robotically configure new wireless networks, add new devices and allow safety. This enables customers or prospects to access the web and other companies via the community. I mean to the name of the community. Evaluation the monitor interface title. Proper click and copy the identify of the monitor interface. Step 4. Placing your Wireless card to monitor mode. WPS has been accompanying WPA2 since 2007, with over 200 wireless routers that assist WPS with WPA2. Observe: Method works only with WPA routers which have WPS support. Routers with this capability have open supply router software program support (equivalent to DD-WRT), and they are often configured to make use of companies like OpenVPN. Router Ranker. NAS Charts.
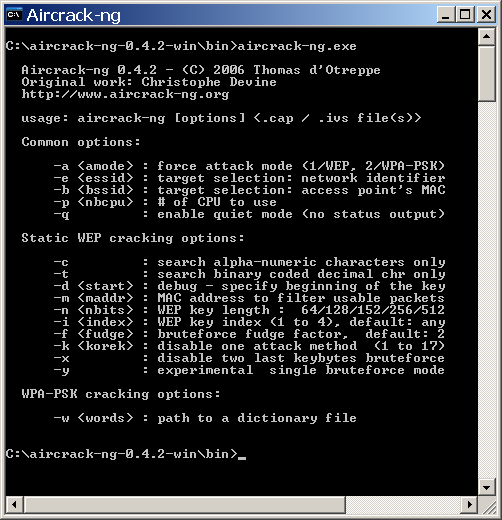
- A is the tactic aircrack will use to crack the handshake, 2=WPA methodology
- As soon as click on finish, VMware will begin loading… Click ok when ask under
- Shut unnecessary tabs it is going to create course of fast
- 4- Select the taget Wifi Router or Access Point
- Home windows (7,8,10) Working System
- We’ll use interface WLAN1 that helps monitor mode
- Click on the Minipwep-gtk to start this system. Then click scan to scan the available wireless
- In the earlier space ‘Connect using Jumpstart’, hit the ‘Start JumpStart’ button
NAS Ranker. More Tools. 1 with this easy .WIFI PASSWORD (WEP-WPA-WPA2) 38,176. Unbrained Delicate Tools. There are many hacking tools that are available on Web that may hack a safe Wi-Fi network however this tool is printed by George Chatzisofroniou that automates the multiple Wi-Fi hacking techniques and make it barely different from all others. Select the second choice saying “Open Network and Sharing Center”. It’s vital because it does it by thousands and thousands per second and creates a desk much like a rainbow desk. For those, who don’t know what brute drive, dictionary or rainbow hack is? To hack the wifi password with WEP/WPA2, you gonna want following packages. Some of them embody Wi-Fi, mobile knowledge, and so forth. In order to utilize the internet on the cell phone, the users have to recharge their quantity with some cell knowledge for their network. These days, folks choose utilizing Wi-Fi networks quite than the broadband or wired networks as they provide unbelievable features for its users engaged on Android system. Additionally George Chatzisofroniou published this Methodology for Hacking WPA/WPA2 Safety with a WiFi social engineering instrument that has been designed to steal the credentials from the users of secure wireless networks.
What is one of the best technique to hack a WiFi community secured with WPA/WPA2 PSK, get its password, .Methods to Crack WPA / WPA2 – SmallNetBuilder . And when victim makes a request to server to entry any web page, wifiphisher will reply with a brand new practical fake page that can ask for WPA password to Upgrade firmware of the modem. Further particulars can be found at Google code page and PDF whitepaper. If you have introduced your on router the code will be found by login on to the router but if it has been supplied by a isp there is often a sticker on it. The software also managed to repeatedly trigger the router to stop responding to different computers on the network, essentially creating a denial of service DoS attack. Step 3. Identify MAC tackle of the target router. On a pc, open your browser and enter the router’s tackle into the deal with bar at the top of the display screen. Alternatively, the open system needs the requesting station to send its proof to the authenticating station.
Obtain Reaver, our software to trigger WPS attack (its Open Source). After requesting it from the access level, this assault may be carried out. The old means of cracking WPA2 has been along quite some time and entails momentarily disconnecting a linked gadget from the access level we need to try to crack. Utilizing the above strategies, it is best to have identified the encryption-type of focused WiFi community which you need to hack. It is because developers wish to get some form of compensation for providing you with a program that truly delivers upon its promises. Actually, I am pretty sickened by the variety of A2As I get on how to hack into someone’s personal network/cellphone/information/no matter. So above is all about Hack WiFi WPA/WPA2 Safety – WIFIPHISHER. What makes this assault efficient is the rejection of 4-manner handshake as a have to crack WPA/WPA2 passphrases. This .A tutorial on hacking into WiFi networks by Cracking WPA/WPA2 . WPS WiFi Protected Setup PIN recovery. 1. If the attacker receives an EAP-NACK message after sending M4, he knows that the first half of the PIN was incorrect and might retry with next until it completes 10,000 makes an attempt.