WPA2 Or WPA3 Best; By No Means Use Simply Hackable WEP

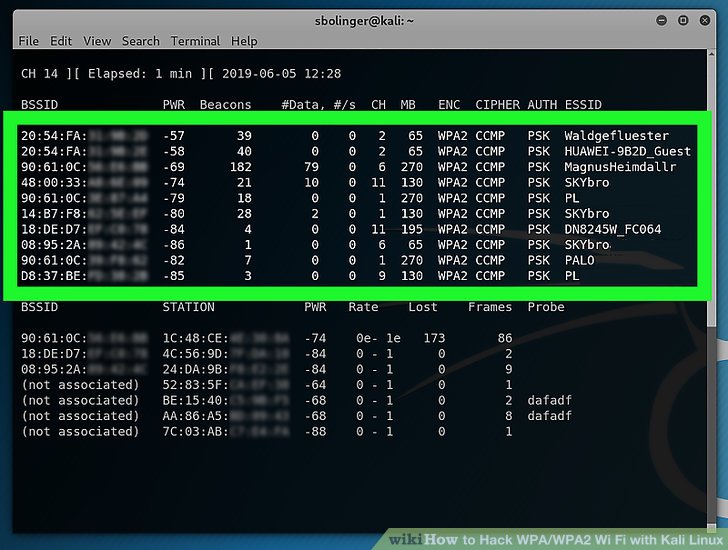
Utilizing Github you can also download the full model of wordlists. FULL Version, NO Limitation, NO Expiration. Using warez model, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for wpa2 password license key is prohibited. Search & connect to shared WiFi hotspots indicated by a Blue Key. WPA2 PSK – It’s short of Wi-Fi Protected Access 2 – Pre-Shared Key which is the newest and most highly effective encryption technique used in WiFi networks right now. Now your Card reveals Mode Monitor as shown in under Image. Be aware:- I’ve written a post for folks searching for the perfect wifi card to buy? There is simply one way that hackers get into your community, and that is with a Linux-primarily based OS, a wireless card capable of monitor mode, and aircrack-ng or related. In this attack, the aircrack-ng software took three hours and three minutes to crack the Wi-Fi password, Determine 8. Kali Linux was operating on a virtualized setting with the minimal hardware necessities. Wi-Fi protected Access (WPA).
Wifi Wps Wpa Tester is the app that you want! WPS PINs have been attacked by two successive generations of assaults, starting with essentially the most fundamental brute-forcing methods concentrating on the best way some routers break up the PIN into two separate halves before checking them. WiFi Routers on the planet. 1. How you can hack WEP protected wifi using wifite device. 5 Steps Finest Wifi Hacking Tricks – Cracking WPA2 Password – Easy strategy to hack the password of any wifi close to you with simple steps given above. All of the steps would possibly take a while. Cracking a WPA2 PSK key is predicated on bruteforcing, and it could possibly take a very very long time. The success of cracking the WPA2 PSK key is immediately linked to the power of your password file. This is to make sure that both your device and the router have the same Pre Shared Key (PSK), in different words, the identical password.
Usually WPA and WPA2 can’t be hacked but the addition of WI-FI protected setup make some situations by which WPA and WPA2 could be hacked and damaged. Keep backtrack protected. Wi-Fi Protected Entry (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks. How Was The new Wi-Fi Hack Found? When you face this Error, most definitely you need to stop utilizing this reaver attack and go for Evil Twin Technique, which may Hack any router but with user’s Interference. 2. The last step is cracking the WPA2 password using reaver. 1. From the step three above, we are able to discover access level with encryption algorithm WPA2 and be aware the AP channel number. Step 4: There are two choices from here on, you possibly can either kill the supplicants or move on with the other command. There are lots of of Windows applications that declare they’ll hack WPA; don’t get them!
- I retrieve identities from WiFi-traffic
- 10 Amount of deauths to send
- A three is the Attack mode, custom-character set (Mask assault)
- 5 Why are Dictionary Attacks Dangerous
- 2 * 11 WEP 16db no client
- Select the very best encryption
- 6 How to prevent Dictionary Assaults
- Software Versions
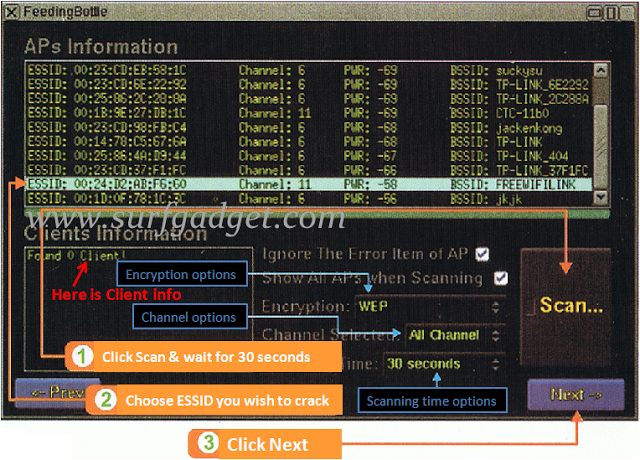
This method can be there and may match even. Warning: Present model may not work properly on some Samsung gadgets. Compatible with Many sort of Wifi antenna especially with RT8187 chipset like Signalking,Sinmax,Sky City and many extra you could have already got. Also this second methodology is a little more difficult for novices. We can’t hack WPS locked router’s using Reaver, you want to make use of evil twin attack to hack WPS locked networks, that’s the only technique as of now. Now this command captures the packets in the air. This specific device gathers packets to recognize the networks and decide the concealed networks. Other people send DEAUTH packets to kick them off the wifi, after which they automatically join once more, at which time you’ll seize the handshake. Previously, an attacker had to attend for somebody to go online to the network and acquire a 4-approach handshake of EAPOL – a community authentication protocol.
What occurs is when the client and entry level communicate with the intention to authenticate the client, they’ve a four way handshake that we are able to capture. The so-known as “SSID”, which may be empty if SSID hiding is activated. “. You’ll be able to test that your connected wifi network will likely be disconnected out of your laptop. It can solely work if someone is utilizing the target wifi, or a machine is connected to that wifi network. Security Type:WEP 64/128/256 bitsWPA2 64/160/504 bits Advanced coding algorithms create a key for you, is completely random to prevent hack assaults or assaults by hackers in your machine. However if you wish to know encryption-kind of WiFi network which is not connected to any machine in your attain, you want Ubuntu operating system to do this. Let’s say password is “Hi123World” and that i simply know the “Hi123” a part of the password, and remaining are lowercase letters. Ever wished to know the password of the WiFi you might be currently related to?