Hacking WPA/WPA2 Wi-fi With Hashcat Full Tutorial 2020

Most importantly, it is best to use the -vv choice, which will increase the verbosity of the instrument. Step-3: Now you should use this password cracking instrument to acquire the WPA PSK (Pre-Shared Key) password and Increase you probably did it! This new WiFi hacking technique may doubtlessly allow attackers to retrieve pre-shared key (PSK) login passwords, allowing them to hack into your Wi-Fi network and communicate with the Internet. Brute Power is very quaint and environment friendly approach of hacking but time consuming. Use a powerful password: Even with this assault, the hacker might want to brute power your password. Nevertheless, it can solely crack it if the password happens to be within the wordlist that you’ve chosen. Within minutes it’ll find your password and it’ll present you the password. If not, then the attack won’t work. Wash is specifically meant to verify whether or not a network has WPS enabled or not, and thereby is way easier to make use of. Use wash (simple however typically unable to detect networks even when they’ve wps enabled). Update : wash -i mon0 –ignore-fcs would possibly solves the problem. Replace : It has nothing to do with internal adapter. Now, in this case, a easy adapter like WN722N would be enough the produce the PMKID.
- Write beini.iso on your USB by UNetbootin. Set the whole lot in response to this image bellow
- 2 ******* eleven WEP 21db no client
- 1PB! We don’t have this free area on our hard disk
- L customizable settings (timeouts, packets/sec, and so forth)
Pairwise Master Key ID (PMKID) will be captured from RSN IE whenever the user tries to authenticate with the router. You may do that by using Kali Linux’s converter. Reaver has a known concern : Sometimes it doesn’t work with Digital Machines, and also you would possibly need to do a reside boot utilizing reside CD or dwell USB of Kali Linux. 4. In case you are using Kali Linux in Vmware, attempt booting into Kali utilizing USB. First off, that you must have Kali linux (or backtrack) up and running on your machine. And if you’re already acquainted with hacking WEP, then just go to your Kali Linux terminal and sort the above command (replacing what needs to be changed). It have great instruments that are used for hacking password. All that I’ve written above (the troubleshooting section) is predicated on personal expertise, and won’t work. My private best is a key every 2 seconds, and yours might drop to as low as a key each 10 seconds. Now in WPS, there’s a delay because we should look forward to APs response, and we could only try a number of keys per second (practically the best I’ve seen on my Laptop is 1 key per 2 sec).
 Depending upon the length of your password record, you might be ready a few minutes to a couple days. 2. Sometimes it never will get a beacon frame, and gets stuck within the waiting for beacon frame stage. 4. You’re very far from the AP. This is what we’re utilizing. Since it allows for networks to help each WPA3 and WPA2 using the identical password, an attacker can create a rogue WPA2 community with same SSID as the unique. And that is all the combos, and most probably the proper pin is not going to be the last mixture, so you possibly can count on to achieve the consequence earlier. Now press enter aircrack will start cracking the Wi-Fi. Sort within the password you employ to log into your laptop, then press ↵ Enter. When your laptop, or your smartphone, or whatever your system is, joins a WiFi community it negotiates what is known as a 4-approach handshake.
Depending upon the length of your password record, you might be ready a few minutes to a couple days. 2. Sometimes it never will get a beacon frame, and gets stuck within the waiting for beacon frame stage. 4. You’re very far from the AP. This is what we’re utilizing. Since it allows for networks to help each WPA3 and WPA2 using the identical password, an attacker can create a rogue WPA2 community with same SSID as the unique. And that is all the combos, and most probably the proper pin is not going to be the last mixture, so you possibly can count on to achieve the consequence earlier. Now press enter aircrack will start cracking the Wi-Fi. Sort within the password you employ to log into your laptop, then press ↵ Enter. When your laptop, or your smartphone, or whatever your system is, joins a WiFi community it negotiates what is known as a 4-approach handshake.
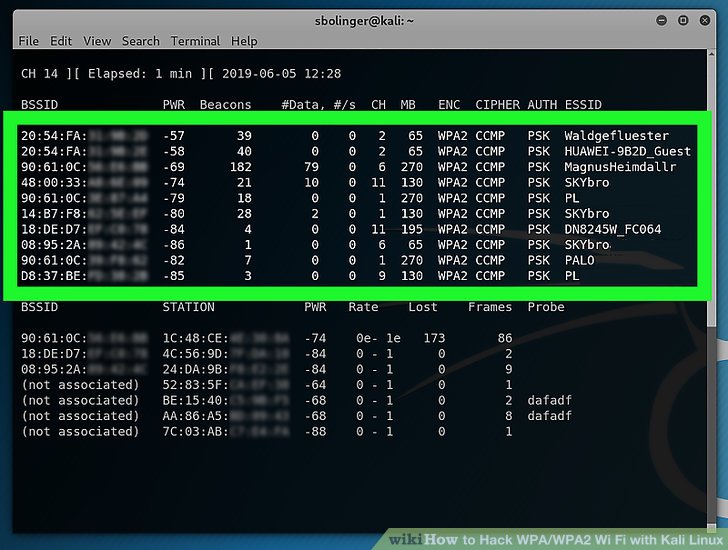
Consumer units in the transition mode will then connect to the rogue community utilizing WPA2, leaving the handshake exposed. We at present do not know how many suppliers or how many routers this technique can use on merchandise, but we expect it can work with 802.11i / p / q / r networks that enable network switching. When you have any problem whereas downloading any software then you may contact me using the contact form or drop a comment. On this tutorial, we’ll use a chunk of software developed by wireless safety researcher Joshua Wright called cowpatty (often stylized as coWPAtty). Use airodump-ng. It will present all networks around you. After some hours, you will note something like this. Nonetheless, the assumption is that bruteforcing will take place at a key per second. This encryption methodology is identifiable by the important thing of 10 or 26 hexadecimal digits. “Typically, previous assaults would require a client to be related to the community in order for visitors to be generated and the key cracked. So principally, the client sends 8 digit pins to the access point, which verifies it and then permits the client to attach.