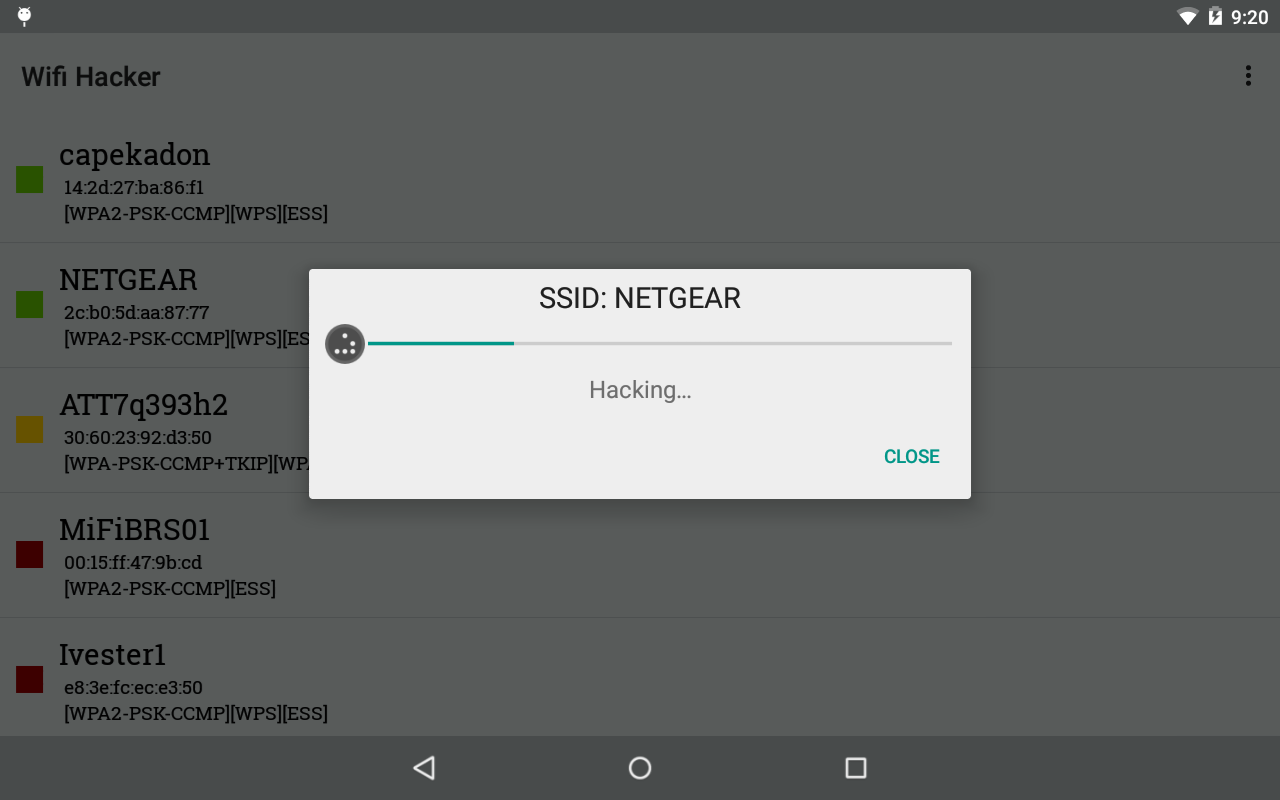
WPA/WPA2 Wifi HACKING PASSKEY Restoration MADE Easy . 7 MOST Powerful WIFI APPS COMPILATION
7. Below proven successful case with password shown. You hacked Wi-Fi password is proven. The challenge right here was to see how to improve the technique to crack a Wi-Fi password. Hack WiFi Password Online. 5 Steps Finest Wifi Hacking Tips – Cracking WPA2 Password – Easy approach to hack the password of any wifi near you with simple steps given above. Relying on your hardware velocity and the scale of your password list, this may take fairly a while to finish. Q. Can I take advantage of the Decoder in multiple pc at the same time? Q. Do I must run the Decoder software Disc boot up every time I want to make use of the WiFi Decoder? A. Go to the BIOS setting and alter the Default Boot As much as Disc Drive. You do this by setting up a very totally different Wi-Fi router or enabling your router’s “Visitor Network” possibility, a popular feature for many routers.

Q. Is it legal to use somebody`s Wi-Fi connection to browse the net in the event that they haven`t put a password on it? Our software can capture, analyze and crack the password with sufficient knowledge. Q: Can I use the Super WiFi in all nations? A. Please use the Agent Inquiry page to contact us. Q. Can I be your agent? A. No, after you have got decoded the passwords of the connection, simply write them down and you can use it for as long as you need, or until the administrator changes the passwords. A. No, After you may have decoded the passwords of the connections, simply write them down and you need to use them for so long as you need, or until the administrator change the passwords. A. Yes, because the WiFi Decoder does not require an AC Adapter, It can be utilized in any place with a Computer or Laptop computer and normal WiFi connections, as WiFi standards are the same worldwide.
- Launch a FakeAP occasion to imitate the unique access point
- If it discovered a password, it should appear like this
- Scan the networks
- Open realteck icon on your desktop and search obtainable network
- After ending restart your Pc and boot it from your USB
- It will close automatically – after getting the appropriate password
 A. Sure, as the Super WiFi don’t require an AC Adapter, It can be used in any place with a Pc or Laptop computer and customary WiFi connections. The WiFi Decoder is so powerful that it could possibly receive WiFi connections as much as 2 km away in open house! On the other hand, the open system wants the requesting station to send its proof to the authenticating station. There are two main types of authentication that embody Shared Key and Open System. Choose one of those methods to open Keychain Access. Wi-Fi Protected Access (WPA) and Wi-Fi Protected Entry II (WPA2) are two safety protocols and security certification packages developed by the Wi-Fi Alliance to secure wireless computer networks. You can learn more about that in my beginner’s guide to hacking Wi-Fi. We counsel that you simply watch the Video Guide and skim the Person Guide first earlier than utilizing the WiFi Decoder. Q. Can the house owners know that I’m utilizing their WiFi connection? Before we can execute the assault, nonetheless, we’ll have to seize the handshake and the password checklist, so let’s grab these first. 4. Click start to assault, you will notice the IVS start running..
A. Sure, as the Super WiFi don’t require an AC Adapter, It can be used in any place with a Pc or Laptop computer and customary WiFi connections. The WiFi Decoder is so powerful that it could possibly receive WiFi connections as much as 2 km away in open house! On the other hand, the open system wants the requesting station to send its proof to the authenticating station. There are two main types of authentication that embody Shared Key and Open System. Choose one of those methods to open Keychain Access. Wi-Fi Protected Access (WPA) and Wi-Fi Protected Entry II (WPA2) are two safety protocols and security certification packages developed by the Wi-Fi Alliance to secure wireless computer networks. You can learn more about that in my beginner’s guide to hacking Wi-Fi. We counsel that you simply watch the Video Guide and skim the Person Guide first earlier than utilizing the WiFi Decoder. Q. Can the house owners know that I’m utilizing their WiFi connection? Before we can execute the assault, nonetheless, we’ll have to seize the handshake and the password checklist, so let’s grab these first. 4. Click start to assault, you will notice the IVS start running..
Because of the MiTM assault, it is possible to extract an encrypted password. And as far as we all know there are not any legal guidelines banning the sharing of an encrypted WiFi connection. There are a number of apps that help the consumer hack a Wi-Fi community password with 100% accuracy. First Wi-Fi signals have been protected utilizing WPS. If you have not seen the other Wi-Fi hacking guides yet, And as all the time, when you’ve got questions on any of this, please ask away within the comments below. With this course you’ll get 24/7 help, so you probably have any questions you can submit them in the Q&A piece and we’ll reply to you inside 15 hours. Now, you might or may not get the warning showing within the beneath screenshot which tells different processes using the network which might create the issue. Now, if I had been planning on writing efficient code to crack WPA2 with PMKID, Python with scapy would have been my priority.