5 Steps Wifi Hacking – Cracking WPA2 Password
 It as an alternative makes the means of acquiring a hash that can may be attacked to get the wireless password a lot simpler. To get entry to the PMKID, this new attack has to try to authenticate to the wireless community later we can simply hack WiFi password and the essential pre-shared behalf of WiFi Hacker. In brief, This tutorial is a “Behind the Scenes” of a Wireless Crack Try. A safety researcher has devised a new WiFi hacking approach that could possibly be exploited to simply crack WiFi passwords of most trendy routers. A brand new technique has been discovered to simply retrieve the Pairwise Grasp Key Identifier (PMKID) from a router using WPA/WPA2 safety, which can then be used to crack the wireless password of the router. New Assault technique for WiFi Hacker found to hack WiFi Password that secured with WPA/WPA2 in WiFi networks that allow attackers to achieve Pre-shared Key hash that used to hack Wifi Password utilized by targeted victims.
It as an alternative makes the means of acquiring a hash that can may be attacked to get the wireless password a lot simpler. To get entry to the PMKID, this new attack has to try to authenticate to the wireless community later we can simply hack WiFi password and the essential pre-shared behalf of WiFi Hacker. In brief, This tutorial is a “Behind the Scenes” of a Wireless Crack Try. A safety researcher has devised a new WiFi hacking approach that could possibly be exploited to simply crack WiFi passwords of most trendy routers. A brand new technique has been discovered to simply retrieve the Pairwise Grasp Key Identifier (PMKID) from a router using WPA/WPA2 safety, which can then be used to crack the wireless password of the router. New Assault technique for WiFi Hacker found to hack WiFi Password that secured with WPA/WPA2 in WiFi networks that allow attackers to achieve Pre-shared Key hash that used to hack Wifi Password utilized by targeted victims.
In this course, I’ve talked in regards to the underlying ideas of what happens after we kind in a password from a phone or a Computer and click on “Connect with WiFi”. I feel that this subject will make operators and companies alike more conscious that they should have central control over WiFi routers, so they can quickly react to specific safety issues by way of firmware patches. I feel that can be completely inappropriate; it’s an unfortunate flaw in a regular, it’s been identified, and might be fixed soon. Also, this assault work In opposition to all kind of 802.11i/p/q/r networks with roaming features enabled and it’s unclear how many distributors and how many routers this method will work. Now we are unsure about which vendors this wifi hack approach will work. The safety researcher Jens ‘Atom’ Steube, lead developer of the favored password-cracking device Hashcat, has devised a brand new WiFi hacking method that might be exploited to easily crack WiFi passwords of most fashionable routers. WPA/WPA2 has been dwindling after the invention of WPA2 key-reinstallation assault (KRACK) and whereas testing the brand new WPA3 protocol, Jens Steube stumbled upon on one other vulnerability in WPA2 protocol, rejecting the need for a handshake to be in place.
“This attack was found unintentionally whereas wanting for brand spanking new methods to attack the brand new WPA3 safety customary. I hope you enjoyed this information to the new PMKID-primarily based Hashcat attack on WPA2 passwords! Step 2 — Utilizing the hcxpcaptool device, the output (in pcapng format) of the body can then be transformed into a hash format accepted by Hashcat. First Run hcxdumptool to gain the PMKID from the AP and dump the file in PCAP format utilizing following code. For the report, if you happen to have a WiFi with WPA only as it is encyption, you are protected from PMKID attack. Let’s just focus on cracking WPA/WPA2 with what we now know as PMKID. The rationale the newer wifi protocols have change into safer is because of the implementation of WPA/WPA2 (wifi protected access) protocols. Many entry point they’ve a Wifi Protected Setup enabled by default (even after we laborious reset the entry point).
- Hcxdumptool -i wlan1mon -o galleria.pcapng –allow__standing=1
- Choose whether or not the network is public or personal and faucet the next button
- WPA + TKIP
- Kind: cd reaver-1.4
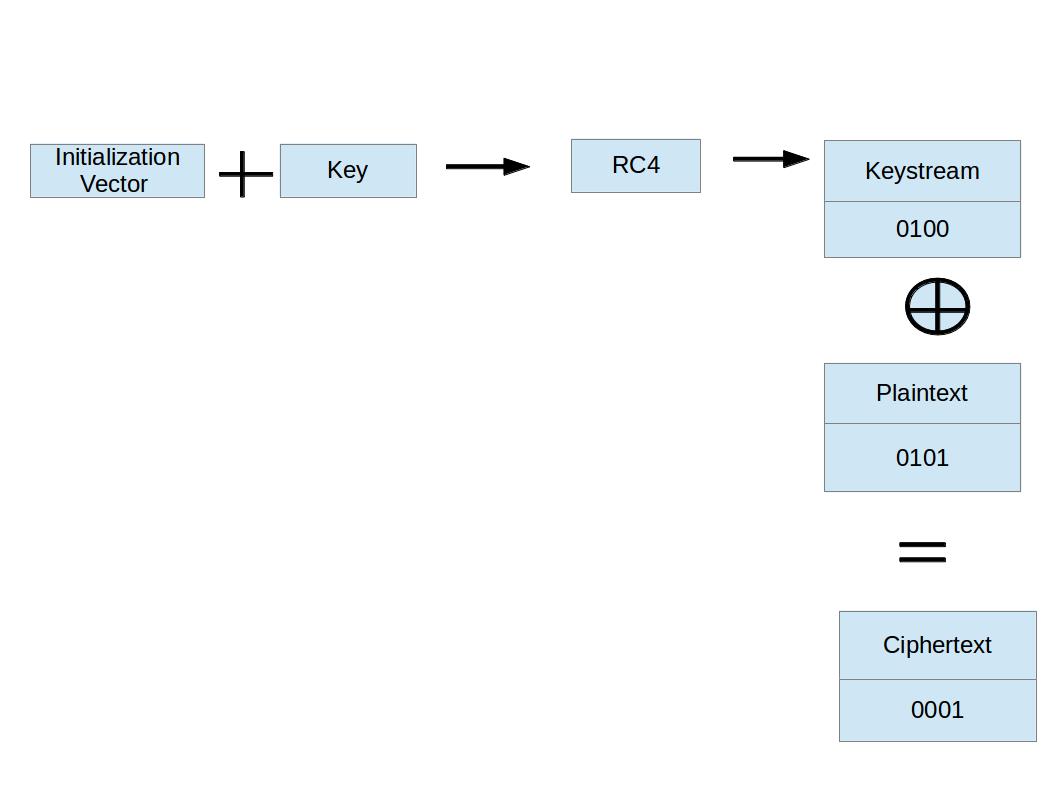
A lately found vulnerability may allow attackers to intercept information being transmitted between a WiFi access level and a pc or mobile gadget, even when that information is encrypted. Am I prone to being hacked? WiFi alerts, particularly WPA2, has been hacked. In keeping with the researcher, the beforehand identified WiFi hacking strategies require attackers to wait for someone to log right into a network and capture a full 4-means authentication handshake of EAPOL, which is a network port authentication protocol. This highly visualized the normal WPA/WPA2 cracking by means of MIC code into a new more sturdy EAPOL capture. However, with the uncovering of this new vulnerability now named PMKID, it is fairly stunning that we are able to skip one of many most vital steps in the normal WPA/WPA2 cracking. We have developed a new assault on WPA/WPA2. Mixing Mask assault with Custom characters. ’s have a have a look at what Mask attack actually is. Shifting on even additional with Mask attack i.r the Hybrid attack.