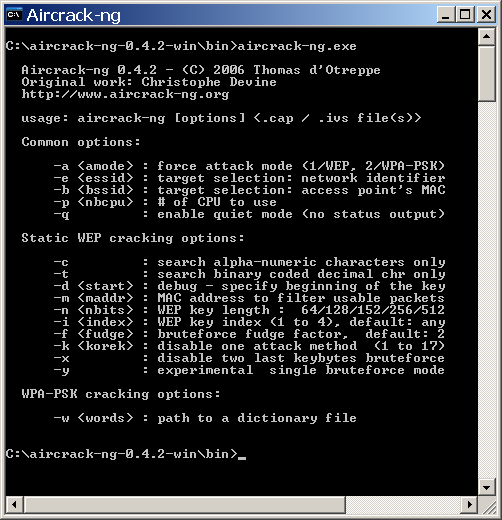
Learn How To Hack: Cracking Wifi Passwords With Cowpatty (WPA2)
Click on on the capture option to start the seize. In case you wish to exclude characters that look related (e.g. letter l and number 1) ensure you choose the Exclude Similar Characters choice. When you wish to obtain with out registering, just hit the “Obtain” button and proceed. Choose the Backtrack Version you wish to download. However, I shall be using Backtrack 5. There is not much difference between the two variations besides that R3 model has extra pre-put in instruments (reaver,wash,and so forth). This will protect the password extra successfully than the other two methods, namely WEP and WPA/WPA2. Java,and so on) you’ll discover this a piece of cake. New safety researchers reveal a new WiFi hacking approach that makes it simple to search out the WiFi passwords of in the present day’s most trendy routers. This new wifi hacking technique was by accident found by Jens Steube lead developer in widespread password-cracking software Hashcat while he was analyzing the newly-launched.
So this reaver is a wifi protected setup assault software. Use airplay-ng -3 -b 64:0F:28:6B:A9:B1 mon0, the place -3 is for ARP REPLAY attack. You could use some other software that can create a Dwell USB. It may take a while for you to deauthenticate the consumer. Be affected person, it’d take some time. Sadly, it will take a few years till WPA3 becomes the norm. It’s going to take round 10 mins to your Dwell USB to be ready. Now we are ready to capture the PMKIDs of devices we wish to try attacking. Attempt them out, and be affected person with it. Be affected person and wait. A. The WEP key is often found between 15,000 and 20,000 IVS, so be affected person. You possibly can rely on this software program for WPA/WPA2 and WEP encryption networks. Earlier than WPA grew to become the de facto standard, WEP had been the WiFi customary for very long time (and nonetheless many routers use WEP encryption).
- U retrieve usernames from WiFi-site visitors
- Brute-Power attack
- How to hack WPA/WPA2 wifi utilizing fluxion. 2. How you can hack WPA/WPA2 wifi using linset
- However In Reaver Methodology Likelihood is 100% (Only if AP Price Limiting Is not Accessible)
- Please follow below picture by follow the numbering and text in crimson shade
We’ve got captured WPA handshake, but now we have to crack it using wordlist attack. This shall be used to know wpa has been captured or not. Should you just want to know how you can hack wifi password (WEP/WPA/WPA2), this publish is about wifi hacking. Download free Beini 1.2.5 for wifi hacking password. To hack the wifi password with WEP/WPA2, you gonna need following packages. Utilizing the above technique now WiFi Hackers can hack the WiFi Password. But I will be using Backtrack 5. Be certain to select GNOME within the Window Manager tab and be sure you obtain a .iso file. Select the GNOME Window Supervisor. A message ought to seem on the highest right corner your airodump-ng window notifying that WPA Handshake is obtained. Save and exit, then watch for the Kali Linux installation window to seem (you may have to restart your laptop yet one more time). This needs to be easy, as it’s included in the Kali Linux repo by default. SEE Additionally: Kali Linux Hacking Tutorial for Inexperienced persons: Learn to Hack Professionally. Kali linux will now try and crack the wifi password. We recommendation you do not try to attack other folks wireless apart from your own.
 In this video I show find out how to attack WPA/WPA2 PSK “secure” wireless networks! RSN is actually a protocol for organising a secure communication through an 802.Eleven wireless network. Packet injection means interfering with different networks by means of constructing packets to seem as if they are part of the conventional communication stream. Offered that you’ve got persistence and you are prepared, anybody can. Now that we’ve obtained a WPA Handshake, the subsequent step is to initiate a dictionary assault on the capture file. The ultimate step is to crack the password using the generated password dictionary. For a dictionary assault, we’ll want a wordlist which is all around the web. If your wordlist accommodates the proper paraphrase, it will be hacked. Am I vulnerable to being hacked? A just lately found vulnerability might enable attackers to intercept knowledge being transmitted between a WiFi access point and a computer or mobile machine, even if that data is encrypted.
In this video I show find out how to attack WPA/WPA2 PSK “secure” wireless networks! RSN is actually a protocol for organising a secure communication through an 802.Eleven wireless network. Packet injection means interfering with different networks by means of constructing packets to seem as if they are part of the conventional communication stream. Offered that you’ve got persistence and you are prepared, anybody can. Now that we’ve obtained a WPA Handshake, the subsequent step is to initiate a dictionary assault on the capture file. The ultimate step is to crack the password using the generated password dictionary. For a dictionary assault, we’ll want a wordlist which is all around the web. If your wordlist accommodates the proper paraphrase, it will be hacked. Am I vulnerable to being hacked? A just lately found vulnerability might enable attackers to intercept knowledge being transmitted between a WiFi access point and a computer or mobile machine, even if that data is encrypted.