WPA/WPA2 Wifi HACKING PASSKEY Recovery MADE Easy . 7 MOST Highly Effective WIFI APPS COMPILATION
According to experiences of specialists in digital forensics from the Worldwide Institute of Cyber Security, this attack technique works in opposition to the wireless network protocols WPA/WPA2 with roaming functions based mostly on Pairwise Master Key identifier (PMKID) enabled. So, we’d like to investigate which of the networks (Access Points) is WPS enabled. C to cease trying to find networks. Lets analyze the out there networks that are WPS enabled. Select WiFi card and anticipate the monitor mode enabled (flip to green shade). Reaver requires the community to be WPS enabled. There are a number of version of reaver. 7- After a few Successful handshake Capture we are ready to Crack the password and get it in Plain Textual content. The weakness within the WPA2-PSK system is that the encrypted password is shared in what is thought because the 4-approach handshake. It’s the encrypted sign most home and workplace routers use. Attackers can use this novel assault method to learn information that was previously assumed to be safely encrypted. Sturdy Security Network Information Ingredient (RSN IE) is an non-obligatory one in 802.Eleven administration frames and its working in a single EAPOL body.
- The size of the password matters so much, it’s an efficient defence against brute-force attacks
- 5 Steps Wifi Hacking – Cracking WPA2 Password
- VMware 12 Pro
- three different safety varieties to choose from
- I, –interface: Monitor Interface to use
Airodump will now list the entire wireless networks in your area, and quite a lot of helpful details about them. Earlier than we hit you with an additional-studying listing of our top Wi-Fi safety articles, here’s the crash course. In case you take a look at on-line documentation, all theories say to make use of Crunch to create a huge phrase list and Pyrit for distributing hundreds to different AMIs. As I acknowledged earlier, we shall use “wash” tool for this. For that we use the “wash” software. Q. Can I exploit the WiFi Decoder on my Notebook Pc? Q. How can the WiFi Decoder discover the password of a secured WiFi connection? With Portable Penetrator you can get well WiFi password. Chances are you’ll watch this video to know easy methods to hack wifi using kali linux using reaver technique. Install Kali Linux. To install Kali Linux on your computer, do the following:- Immediate your Home windows laptop to restart. Copy this file to one among your native drives in your Onerous Disk apart from your Home windows Drive (i.e drive where your Windows is installed).
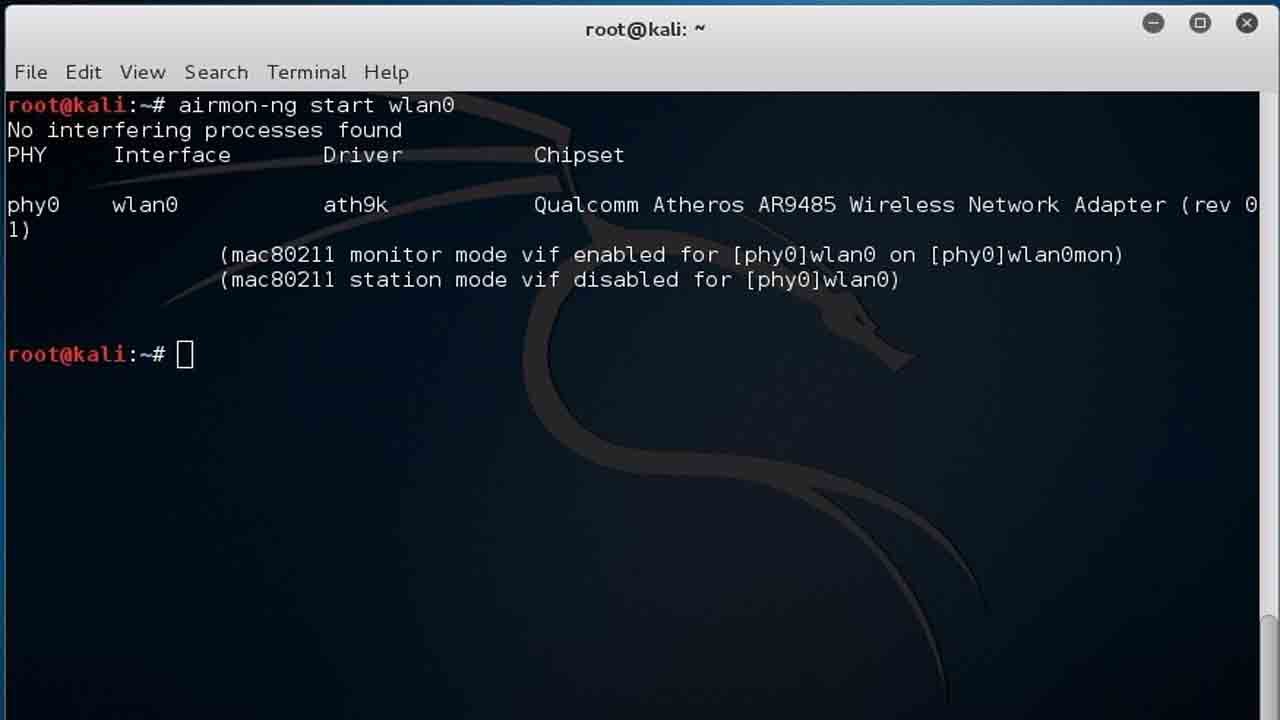 It means you can boot any Operating System from your Home windows. Simply choose the Default Boot Textual content Mode and hit enter. 2. Open terminal and kind in airmon-ng and hit enter, after that type airmon-ng begin wlan0 and once more hit enter. Type ” startx ” and hit enter as in picture below. The location of Terminal tab is shown in the picture below. Please wait till the “Key Found” as show in below picture. This command will show your entire wireless network interfaces. The Wpa teser app will show you the pretend backtrack 5 animations which analyse the wifi cacker and show hacking proccess. A. You should use the spoonwpa to decode WPA encryption but it’ll take much longer and it may not work every time. We’ve captured WPA handshake, however now we must crack it using wordlist assault. Airodump-ng will now monitor all of the wireless networks obtainable in your area. But as I stated earlier, not all of these networks can be hacked by Reaver. But for Backtrack 5, you’ll need to put in Reaver.
It means you can boot any Operating System from your Home windows. Simply choose the Default Boot Textual content Mode and hit enter. 2. Open terminal and kind in airmon-ng and hit enter, after that type airmon-ng begin wlan0 and once more hit enter. Type ” startx ” and hit enter as in picture below. The location of Terminal tab is shown in the picture below. Please wait till the “Key Found” as show in below picture. This command will show your entire wireless network interfaces. The Wpa teser app will show you the pretend backtrack 5 animations which analyse the wifi cacker and show hacking proccess. A. You should use the spoonwpa to decode WPA encryption but it’ll take much longer and it may not work every time. We’ve captured WPA handshake, however now we must crack it using wordlist assault. Airodump-ng will now monitor all of the wireless networks obtainable in your area. But as I stated earlier, not all of these networks can be hacked by Reaver. But for Backtrack 5, you’ll need to put in Reaver.
When you enter the eight commands, your reaver is now put in and prepared to make use of. After the burning is over, your dwell DVD is prepared. It is going to take round 10 mins on your Dwell USB to be prepared. Everybody has their own take on it. This will take a very long time. 5W”, properly not at all times, WPS hacking is round for quite a while. Now You are all set for hacking. And you are all set for hacking. Also, this attack work Towards all type of 802.11i/p/q/r networks with roaming features enabled, and it’s unclear what number of distributors and how many routers this technique will work. Each of these are safety protocols and security certificates developed by the Wi-Fi Alliance to protect your Wi-Fi networks from unauthorized access. After requesting it from the entry point, this assault will be performed. In case you are unable to open Keychain Access using one technique, attempt another method to open it.