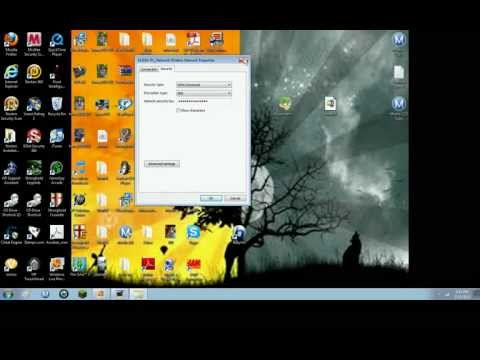
WPA/WPA2 Wifi HACKING PASSKEY Restoration MADE Straightforward . 7 MOST Powerful WIFI APPS COMPILATION
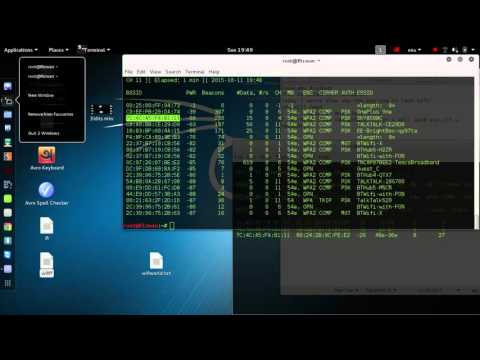 It may take some time so that you can deauthenticate the consumer. Now whereas a lot of the things are the same as in WPA, there’s a brand new idea of using pins for authentication. Now that we’ve obtained a WPA Handshake, the following step is to provoke a dictionary assault on the capture file. AES. Every little thing else on the checklist is a lower than ultimate step down from that. There’s a listing of Community Adapters which might be suitable with Backtrack and able to injecting packets. So we begin an airodump to seize the packets from the AP. Notice the name of your capture file. You can accomplish that by typing in the next command and urgent ↵ Enter: airmon-ng begin wlan0- Make sure you replace “wlan0” with the title of your goal community if it’s totally different. You will also want a Wifi network adapter for this. If in case you have Backtrack 5,then you definitely will need to download “reaver” and set up it. Gorodyansky defined that the adversary would also have entry to any attached storage. Now all we have to do is capture a WPA Handshake from the AP (access level).
It may take some time so that you can deauthenticate the consumer. Now whereas a lot of the things are the same as in WPA, there’s a brand new idea of using pins for authentication. Now that we’ve obtained a WPA Handshake, the following step is to provoke a dictionary assault on the capture file. AES. Every little thing else on the checklist is a lower than ultimate step down from that. There’s a listing of Community Adapters which might be suitable with Backtrack and able to injecting packets. So we begin an airodump to seize the packets from the AP. Notice the name of your capture file. You can accomplish that by typing in the next command and urgent ↵ Enter: airmon-ng begin wlan0- Make sure you replace “wlan0” with the title of your goal community if it’s totally different. You will also want a Wifi network adapter for this. If in case you have Backtrack 5,then you definitely will need to download “reaver” and set up it. Gorodyansky defined that the adversary would also have entry to any attached storage. Now all we have to do is capture a WPA Handshake from the AP (access level).
That permits them to simply break in to your WiFi entry level. What you need is you, the attacker, a shopper who’ll connect with the wireless network, and the wireless entry point. Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two safety protocols and safety certification programs developed by the Wi-Fi Alliance to secure wireless computer networks. It’s used to interrupt into a pc system or server that’s protected by the password by systematically getting into each word in the dictionary as a password. For a dictionary attack, we’ll need a wordlist which is all over the web. The primary difference from existing assaults is that in this assault, seize of a full EAPOL 4-way handshake will not be required. The new attack as a substitute is carried out on the RSN IE, the Robust Safety Community Info Factor, of a single EAPOL body. In general, wireless internet thought of as the network via which the users can make use of internet companies. Nonetheless, the FWF offers no warranty as to the accuracy, completeness or foreign money of the content and will make modifications in content material, advertising, merchandise, different supplies, goods or services described herein at any time. However, this hacking tutorial is efficient only for WPS enabled networks.
- Wireless Card(Inbuild or External)
- Kind http://192.168.2.1 in the tackle bar and press Enter
- The AP doesn’t use WPS
- 2019 Top Programming Languages Used in Hacking
- Select the wifi ssid you wish to crack
Nonetheless, I might be using Backtrack 5. There just isn’t much difference between the two variations besides that R3 version has additional pre-installed tools (reaver,wash,and so on). Beini additionally supported and integrated with Bottle Feeding module in all variations of Beini and just like the minidump-gtk, is one in every of the easiest and quickest strategies to audit the safety degree of our wireless community. Whereas, the not requires one other user to be on the goal network to capture credentials. Steube’s attack methodology, although, doesn’t require an finish user. ’s have a look at what Mask attack actually is. If in case you have been a sufferer of this then this Wi-Fi password app could be your ally in your battle in opposition to Wi-Fi hackers. Step 2 — Utilizing the hcxpcaptool instrument, the output (in pcapng format) of the body can then be converted into a hash format accepted by Hashcat. After you’ve got downloaded Backtrack 5, the subsequent step is to create a stay USB or live DVD for booting up Backtrack. We might be utilizing this file later to create a Stay USB (or a Reside Bootable DVD).
Boot your Laptop from the Dwell USB or Live DVD (not your Laborious Disk). For creating a Dwell USB you’ll want a software Unetbootin. It’s possible you’ll use some other software program that can create a Live USB. It’s going to take round 10 mins for your Stay USB to be ready. Once you hit enter to this command, it’s going to begin testing all of the words current in the wordlist. After we enter the above command, it can begin sending DeAuthenticating Packets. After coming into the above command, it is going to start capturing packets from the AP. After you hit the obtain button, the above page will show up. Java,etc) one can find this a chunk of cake. So if you don’t have Backtrack, it is strongly recommended to obtain Backtrack 5 R3 (you is not going to have to put in reaver). Should you do not need this software program, simply google it and download it. Offered that you’ve got endurance and you might be prepared, anybody can.