Cracking Wifi WPA/WPA2 Passwords Utilizing Pyrit Cowpatty In Kali Linux
This whole process was used in Kali Linux and it took me lower than 10 minutes to crack a Wifi WPA/WPA2 password utilizing pyrit cowpatty WiFite mixture using my laptop working a AMD ATI 7500HD Graphics card. Why WiFite as an alternative of other guides that uses Aircrack-ng? This is definitely a terrific feature of WiFite. When you want to be taught Wi-Fi password hacking, this newly found flaw in WPA/WPA2 protocol will certainly show you how to out. It will disconnect a particular clinet on Entry Level ( Router ) to get Handshake Rapidly. And voila, took it only few seconds to capture a handshake. To name a couple of. Utilizing Hashcat is an good possibility as if you possibly can guess 1 or 2 characters in a password, it only takes few minutes. For people who wish to achieve entry to WiFi networks which might be secured, having a WPA2 password cracker could do a lot of fine.
WIFI PASSWORD (WEP-WPA-WPA2) is a good utility app which allows you to make sure the safety of your Wi-Fi connection by providing you random passwords for protecting your Wi-Fi. Readers, those who wish to attempt alternate methods of cracking Wifi WPA WPA2 passwords, use HashCat or cudaHashcat or oclHashcat to crack your unknown Wifi WPA WPA2 passwords. With Portable Penetrator you can recuperate WEP WPA WPA2 Keys. The keys used by WPA are 256-bit, a major increase over the 64-bit and 128-bit keys used in the WEP system. We’re intrested solely in BSSID and Chanel as a result of rest we are going to crack. You can also make rules to solely strive letters and numbers to crack a completely unknown password if you understand a sure Router’s default password comprises only those. Because these attacks rely on guessing the password the Wi-Fi community is using, there are two common sources of guesses; The primary is customers picking default or outrageously unhealthy passwords, reminiscent of “12345678” or “password.” These will be simply cracked.
- Apt install hashcat
- To use the .cap in the hashcat first we will convert the file to the .hccapx file
- Remember to change “mon0” with whatever your interface identify was
- 1 Crack WPA/WPA2 Wifi Password utilizing Fluxion1.1 What is Fluxion
- Obtain and install JumpStart, WinPcap, and Dumper
- A USB pen drive
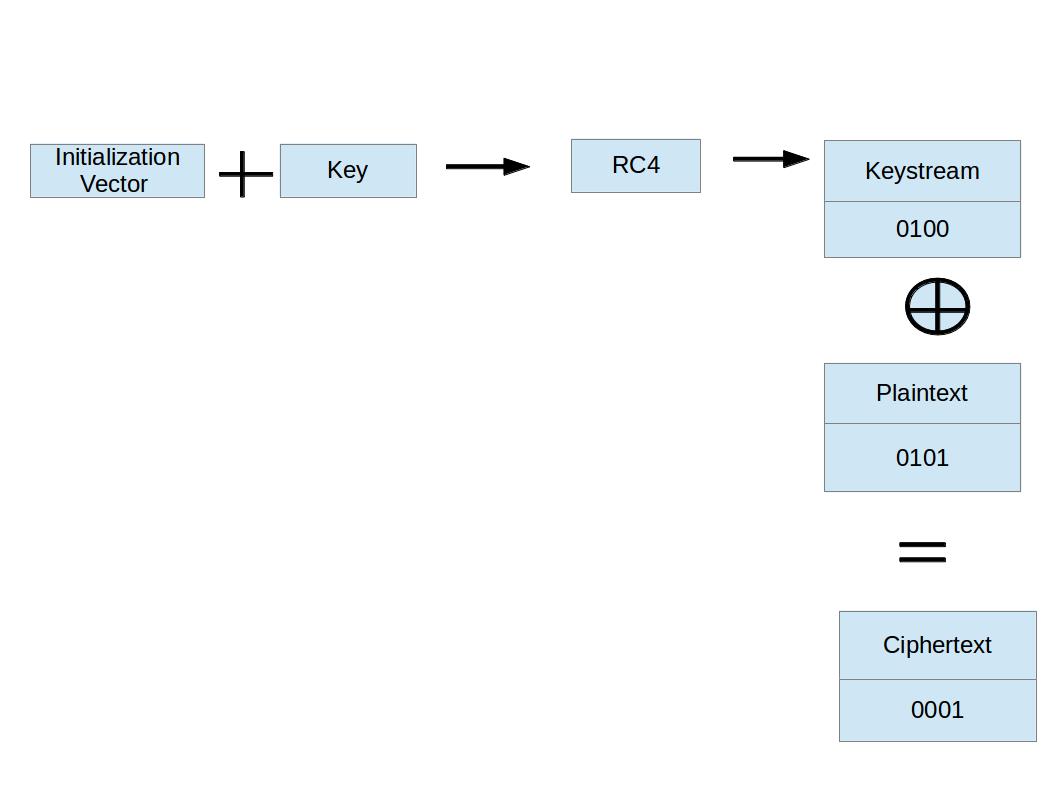
- sixteen bytes of EAPOL-Key Affirmation Key (KCK)- Used to compute MIC on WPA EAPOL Key message
- Chipset: Realtek RTL8188CUS
Even if you happen to search on YouTube you will find a lots of tutorial to The right way to hack a WiFi password utilizing backtrack. This new WiFi hacking methodology could doubtlessly permit attackers to retrieve pre-shared key (PSK) login passwords, permitting them to hack into your Wi-Fi network and communicate with the Web. Since the new WiFi hack only works on networks with enabled roaming functions and requires attackers to power brute passwords, it is recommended that users protect their WiFi network with a secure password that’s difficult to crack. Brute force is essentially the most sure-fireplace way, however I discover it time-consuming, useful resource-consuming and really un-elegant. If you’re unable to find your password, contact your ISP for assistance. If you have an interest. As soon as the username and password have been accepted and you might be in the routers internal settings you’ll be able to navigate to the security tab or administration tab depending on the particular brand of router that you’ve got. That is the wireless network’s password, which might take time relying on its size and complexity. Relying on your hardware pace and the scale of your password listing, this can take fairly some time to complete.
At this time i am going to show you tips on how to a crack a Wp2-psk password with home windows machine. Right now I’m gonna tell you. Attempt all of the features of Passcovery Suite (including restoration of WiFi passwords from WPA/WPA2 handshakes) before purchasing the program. Passcovery Suite recovers WiFi passwords from captured WPA/WPA2 handshakes. The 123 is the data which passwords could be created from, the passwords can only contain the numbers 1, 2 or 3. As proven under. In any other case, for now, the neatest thing you are able to do is make certain that you’ve got a robust password in your network. However you produce other assault choices are also obtainable. Steube by accident found the assault to compromise the WPA / WPA2 enabled WiFi networks whereas analyzing the newly launched WPA3 security standard. While the new attack towards Wi-Fi passwords makes it simpler for hackers to attempt an assault on a goal, the same strategies that have been effective towards earlier kinds of WPA cracking remain efficient. Whereas wanting for ways to assault the new WPA3 security standard, Hashcat developer Jens “Atom” Steube found a easier method to seize and crack access credentials defending WPA and WPA2 wireless networks. The brand new assault doesn’t require one other user to capture credentials on the goal community.
The benefit of utilizing Hashcat is, you may create your personal rule to match a pattern and do a Brute-pressure attack. That is an alternate to using dictionary assault where dictionary can comprise only sure quantity of phrases but a brute-force assault will permit you to check every attainable mixtures of given charsets. In this information, I will show Dictionary assault as almost 20% (that’s 1 in each 5) AP’s may have a regular dictionary password. 6 How to forestall Dictionary Assaults? Please bear in mind that assaults by WPA / WPA2 are illegal except you may have permission from the community owner and the events involved. I have a wordlist known as “wpa.txt” in the basis folder. This occurs with the help of software referred to as My WiFi Router. Software program searches .hccap (hashcat cap) and .wpah information. Jens Steube not simply publicly published the vulnerability along with his software hashcat but in addition disclosed much wider information and allowed us to dissect our personal frames to acheive a lot greater aims. The brand new WiFi hack, found by the lead developer of the popular Hashcat password cracking instrument, Jens’ Atom’ Steube, explicitly works against WPA / WPA2 wireless network protocols with enabled roaming features primarily based on the Pairwise Master Key Identifier (PMKID).