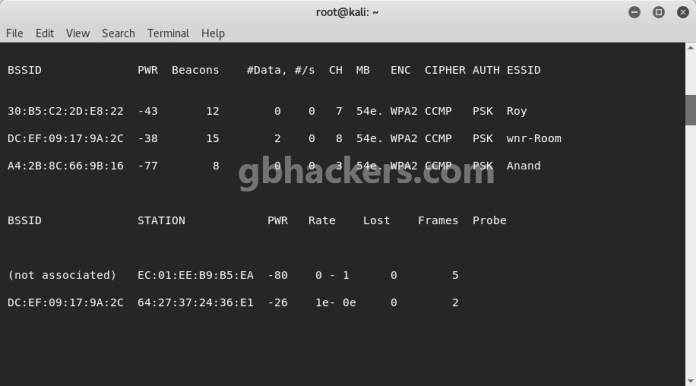
Cracking Wifi WPA/WPA2 Passwords Utilizing Pyrit Cowpatty In Kali Linux
Previously, on this tutorial we had lined doing the same assault by way of a unique perspective, basically following the foot-steps of Jens Steube via completely different instruments. And, it’s the time to make you are feeling the same. Open the flash drive, then drag the downloaded Kali Linux ISO file into the flash drive’s window.- Ensure you depart your USB flash drive plugged in after you finish this course of. The file will be reused in various other circumstances including the well-known hashcat software. Its not a standard .txt file so I’m unsure, or may i just change it into a txt file and be wonderful? Change The ‘bssid‘ and ‘channel‘ according to the output of step 3. Generally, Bssid is mac deal with of Any wifi network device. Now enter this command “reaver -i wlan0mon -b (Paste the Copied Bssid) -vv -K 1“. And hit enter. Hit the ‘Scan’ button now.
- Does this method really work
- I, –interface: Monitor Interface to use
- Join a machine to the router with Ethernet cable i.e. your MAC
- W path to word list in my case it’s ‘/root/Desktop/wordlist.txt’

6. Hit the ‘Scan’ button. 11. Finally, select the targeted community from before and hit ‘Next’.Now you’re fortunately related to that WiFi network you simply penetrated. 12. Open the menu the place you be part of WiFi networks/view the network you’re related to. Return to the background Terminal window when you’re performed sending the deauth packets. To do that, sort the next command right into a terminal window, substituting the identify of your wireless network adapter for wlan0. This activity is dependent upon the type of password and available hardware. It’ll let you join with no password, then you can get the password from inside the community. You’ll be able to then begin accessing the software. Some routers can blacklist you for couple of minutes after 50 attempts, however excellent news is that the majority routers don’t. WPS has been accompanying WPA2 since 2007, with over 200 wireless routers that support WPS with WPA2. Notice: Technique works solely with WPA routers which have WPS assist. Strive ManualsLib or ManualsOnline, which both have lots of of 1000’s of manuals, from routers to refrigerators to anything else you may want. In accordance with the researchers, you additionally don’t want a consumer who logs into the goal community with the intention to seize his login information (one thing that was crucial earlier than) since the attacker now communicates immediately with the entry level.
If each of the requests are to be efficiently performed, each the station and the access level have to be agreed upon some phrases. 1. Firstly Sufferer is being deauthenticated from its entry level and the this software program continuously jams all the target devices on the entry factors by altering the entry point of all the device by way of the primary server. In this instance, I will probably be cracking An iPhone private hotspot which is password protected with the password being “password”. It tries every doable combination of phrases, letters, symbols, numbers and eventually gave the password. Dictionary hack uses the dictionary for hacking the password, it tries all the combination of words accessible in dictionary and if the password is combination of dictionary words, then this methodology is the very best method to hack any password. Now there’s no direct means of getting the password out of the hash, and thus hashing is a strong safety methodology. Here is the method to hack wifi WPA/WPA2 secuirty utilizing WIFIPHISHER. Utilizing warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for wpa2 password license key is prohibited.
Be taught how one can hack your WPA WiFi Password to make it secure. As background, Mathy Vanhoef from the College of Leuven, identified a difficulty in the WiFi normal itself and has now alerted the general public with a white paper to guantee that the problem will get fastened. So how did the usual encryption choice for securing WiFi networks change into so susceptible to cyberattacks? This was made by the creator to demonstrate weaknesses in wireless networks and for academic functions only. Wireless cards work particularly modes such b, g, n and so on. I’ve my cellphone making a wireless network named ‘me’ protected with wpa-2. We now have plenty of Wi-Fi hacker apps available for android to crack a Wi-Fi community password. 1 with this easy .WIFI PASSWORD (WEP-WPA-WPA2) 38,176. Unbrained Gentle Instruments. WIFI PASSWORD (WEP-WPA-WPA2) affords you the prospect to strengthen your Wifi password. So, they came up with a superb resolution which no different password restoration instrument gives constructed-in at this second.
If you happen to do assume so, then you might be utterly mistaken. 15. The password will then reveal itself. We’ll concentrate on how you can crack a Wi-Fi WPA2 password. Easy methods to Crack WPA / WPA2 Router Charts. Wireless The right way to The right way to Crack WPA / WPA2. Desk 1: Attacking System Specs The oldsters at Distant Exploit have simply launched a brand new beta, BackTrack .WPA2/WPAwifi,WPS .A step-by-step guide to cracking WPA and WPA2 Wifi passwordsWelcome, my hacker novitiates! Step 3. Identify MAC deal with of the target router. You can use any Wifi Scanner like iwScanner (obtain) to notice the MAC deal with of the target Wifi SSID. To take this a bit further, activate MAC (Multimedia Access Management) filtering. WPS is activated by default on all gadgets I had access to. Principally, a Laptop like home windows 7 can act as a Registrar for your Wifi router, and assists in authenticating different units to your WPS enabled Wirelesss network. Step-2: Using the hcxpcaptool , the output (in pcapng format) of the frame could be converted into a hash format accepted by Hashcat like this. In the mean time we are going to cowl utilizing oclHashcat on Windows 8.1 utilizing a Nvidia GPU. Brute Force could be very quaint and environment friendly way of hacking however time consuming.