The Right Way To Hack WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-ng
 This new methodology was discovered by Jens “atom” Steube, the developer of the favored Hashcat password cracking tool, when looking for new ways to crack the WPA3 wireless safety protocol. Design flaws in lots of routers can enable hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a robust password. 64-bit encryption. When the restrictions were lifted, it was elevated to 128-bit. Despite the introduction of 256-bit WEP, 128-bit remains certainly one of the commonest implementations. Regardless of various enhancements, work-arounds, and other makes an attempt to shore up the WEP system, it stays extremely vulnerable. While WEP networks are easy to crack, most straightforward methods to crack WPA and WPA2 encrypted Wi-Fi rely on the password being unhealthy or having the processing power to churn by means of enough outcomes to make brute-forcing a sensible method. Techniques that depend on WEP should be upgraded or, if safety upgrades usually are not an option, changed. Nevertheless, with upgradings and the continuous evolving of scapy, the layers and the fields inside are slightly displaced from their orignal locations. Even in case you are cracking md5, SHA1, OSX, wordpress hashes.
This new methodology was discovered by Jens “atom” Steube, the developer of the favored Hashcat password cracking tool, when looking for new ways to crack the WPA3 wireless safety protocol. Design flaws in lots of routers can enable hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a robust password. 64-bit encryption. When the restrictions were lifted, it was elevated to 128-bit. Despite the introduction of 256-bit WEP, 128-bit remains certainly one of the commonest implementations. Regardless of various enhancements, work-arounds, and other makes an attempt to shore up the WEP system, it stays extremely vulnerable. While WEP networks are easy to crack, most straightforward methods to crack WPA and WPA2 encrypted Wi-Fi rely on the password being unhealthy or having the processing power to churn by means of enough outcomes to make brute-forcing a sensible method. Techniques that depend on WEP should be upgraded or, if safety upgrades usually are not an option, changed. Nevertheless, with upgradings and the continuous evolving of scapy, the layers and the fields inside are slightly displaced from their orignal locations. Even in case you are cracking md5, SHA1, OSX, wordpress hashes.
Even if your network is vulnerable, a robust password continues to be the perfect defense towards an attacker gaining access to your Wi-Fi community utilizing this or another password cracking attack. In case your community does not even help the robust security component containing the PMKID, this assault has no chance of success. I personally suppose that it will assist to additional enhance WiFi safety as it is going to create extra emphasis on the problem. There is no extra complete 4-way handshake recording required. They may then seize the four-method handshake to be able to crack the key. When we take a look at previously available WiFi Hacking attacks for WiFi Hackers, we need to sit again and wait until the goal consumer logged in later we can crack the important thing by capturing the four-manner handshake. Listed below are a couple of examples of how the PSK would appear like when passed a particular Mask. Once they are deauthed, they are going to routinely connect to your faux WiFi. Here is the place you can not get lazy, you will need a convincing, legit-trying page that can persuade at the least one person to enter the WiFi password onto it.
- Brute-Drive assault
- CommView for Wifi ( Obtain)
- Store the captured packets in a file
- 0 Deauth Attack
- The router which you are trying to hack has wps locked or dose not comprise wps enabled
- Within the Keychains listing, click on Native Items
- WPA or WPA2 – WPS Networks Out there with at least 16% sign
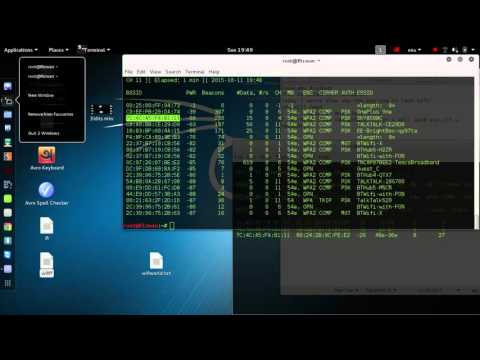
How lengthy to crack a WPA/WPA2 wireless password? We have developed a new assault on WPA/WPA2. This extremely visualized the standard WPA/WPA2 cracking by way of MIC code into a brand new extra sturdy EAPOL seize. It should present you the line containing “WPA” and corresponding code. By running airodump-ng wlan0 our wireless interface will begin capturing the data. Breaking this down, -i tells the program which interface we are utilizing, in this case, wlan1mon. With Portable Penetrator Software you get an easy userfriendly GUI interface. Hack into your individual WPA WiFi entry point and get the password. To get entry to the PMKID, this new assault has to attempt to authenticate to the wireless community later we can easily hack WiFi password and the crucial pre-shared behalf of WiFi Hacker. In addition to, simply the wordlist, wifibroot will attempt to guess the key by making assumptions by means of default passwords and additional reshuffle them in a approach the most firms does with their routers.
The second source of password guesses comes from data breaches that reveal tens of millions of real person passwords. If you discover the password without a good battle, then change your password, if it’s your community. To do this, a trendy wireless attack framework called Airgeddon is used to search out weak networks, and then Bully is used to crack them. To do that attack, you will need to be running Kali Linux and have entry to a wireless network adapterthat helps monitor mode and packet injection. If you’re very near the community, you would try a WiFi spoofing tool like wifi-honey, to try to fool the system into pondering that you’re the router. Start the Hashcat cracking software (v 4.2.Zero or higher versions) and decrypt it. Run subsequent device known as hcxpcaptool to transform the captured data from pcapng format to a hash format accepted by hashcat using following code. In the same folder that your .PCAPNG file is saved, run the following command in a terminal window. Go away airodump-ng running and open a second terminal.
 Sort airodump-ng followed by the identify of the new monitor interface, which is probably mon0. After plugging in your Kali-appropriate wireless network adapter, yow will discover the name by typing ifconfig or ip a. It as an alternative makes the technique of buying a hash that can could be attacked to get the wireless password a lot easier. WeWork workplaces use the same WiFi password throughout many areas and make use of the weak WPA2 Private safety protocol, creating potential for abuse — The We Company sees itself as a world-changing tech platform. Disclaimer: All content in this text is intended for safety research purpose solely. This is somewhat more convenient than just resetting the router with the button on the again, but in addition a massive security gap because of the best way many routers deal with implementing this feature. WPS PINs have been attacked by two successive generations of attacks, beginning with essentially the most basic brute-forcing methods targeting the way in which some routers break up the PIN into two separate halves before checking them.
Sort airodump-ng followed by the identify of the new monitor interface, which is probably mon0. After plugging in your Kali-appropriate wireless network adapter, yow will discover the name by typing ifconfig or ip a. It as an alternative makes the technique of buying a hash that can could be attacked to get the wireless password a lot easier. WeWork workplaces use the same WiFi password throughout many areas and make use of the weak WPA2 Private safety protocol, creating potential for abuse — The We Company sees itself as a world-changing tech platform. Disclaimer: All content in this text is intended for safety research purpose solely. This is somewhat more convenient than just resetting the router with the button on the again, but in addition a massive security gap because of the best way many routers deal with implementing this feature. WPS PINs have been attacked by two successive generations of attacks, beginning with essentially the most basic brute-forcing methods targeting the way in which some routers break up the PIN into two separate halves before checking them.