The Way To Crack WPA-WPA2 PSK Enabled WiFi Network Passwords?
Relying on the size and complexity of the password and the power of the cracking rig, that last step might take hours or days. You can go for brute power attack in such cases but it would take a variety of time depending on your computer system. It might take a long time, or it’d only take a second earlier than the primary one exhibits. So, even in fastest laptop you can manage to use, it’s going to take hours. So After the Above Steps, We Must have the Handshake Packets and likewise We Should have WordList as we talked Above that you could Google That For newest WordList. Fluxion use similar 4-way handshake method to crack secured WPA/WPA2 WiFi access factors password but it doesn’t require you to have dictionary or carry out brute power attack. You see, we try to capture a 4-means handshake by forcing the purchasers to re-authenticate with the Entry level by forging those savage de-authentication frames.
- Once completed scan, it’ll show you out there wireless in your space. Refer picture beneath
- The BSSID of the network
- After that you have to follow given video tutorial for hacking wifi password with it
- Each submitted password is verified by the handshake captured earlier
- Mannequin: TL-WDR3600
- Open Authentication
- Make set up
- Encryption: WPA2-PSK AES
The approach used to crack WPA/WPA2 WiFi password is 4-way handshake for which there’s a requirement to have at the very least one machine related to the network. The wordlists that you can get online including those that we are going to share for you listed here are a collection of common and uncommon passwords that were utilized by actual individuals at the very least once. In different words there are usually not a lot of people around me that might try to steal or crack my password. In accordance with an estimate, about 80% of the people reuse their passwords on on-line platforms like private banking, social media and even work system. In case you have bother in remembering long passwords then you may make a passphrase. Make sure that to exchange wlan0 in command with the interface identify that your card have. By working airodump-ng wlan0 our wireless interface will begin capturing the info. The Apple router by default has no wireless password..
Because these attacks rely on guessing the password the Wi-Fi network is using, there are two common sources of guesses; The primary is customers selecting default or outrageously dangerous passwords, comparable to “12345678” or “password.” These can be simply cracked. With this feature, it allows customers to put Web-of-Things appliances on a separate community, shielding your central computers and other private gadgets from attacks. 5 Why are Dictionary Attacks Harmful? Four What’s a Dictionary Assault? If an empty PMKID is acquired, you may be informed of the occasion and might be notified that access level is just not fallible to this attack. WPA2 PSK – It’s in need of Wi-Fi Protected Access 2 – Pre-Shared Key which is the newest and most highly effective encryption technique used in WiFi networks right now. Every security protocol we have seen has had some type of situation (generally crippling), however the still-young Wi-Fi Protected Access protocol model 3, aka WPA3, stays susceptible to assault, due to some pretty severe design flaws. This can be a perform of age, backwards compatibility, and the fact that it seems first in the protocol choice menus in many router management panels. Before shifting directly to the methods to hack WiFi networks lets first see what sort of safety and authentication strategies are implemented in WiFi networks.
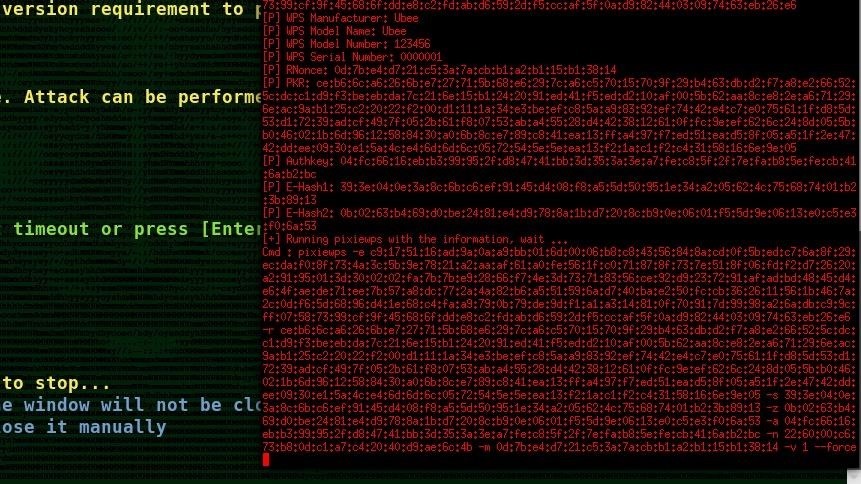
Almost each password-protected WiFi networks help both WPA/WPA2 PSK authentication. Criminals love unsecured residence Wi-Fi networks. Wi-Fi signals (shown under). Now your Card shows Mode Monitor as proven in beneath Picture. And naturally, mon0 merely means the monitor interface, change it if yours is completely different. Open a terminal in Kali Linux and put the Wifi card in Monitor mode Just by typing these commands. One other necessary requirement is to examine if your wireless card is suitable with Aircrack-ng or not. Hashcat will now test in its working listing for any session previously created and merely resume the Cracking process. It focuses on totally different area of WiFi safety: monitoring, attacking, testing and cracking. State of the art Wi-Fi Pen Testing Portable Penetrator Software you’ll be able to recover WPA WiFi Password. Step-2: Utilizing the hcxpcaptool , the output (in pcapng format) of the body may be transformed right into a hash format accepted by Hashcat like this.
They may be labeled otherwise, however search for options under your router’s advanced settings like NAT filtering, port forwarding, port filtering and services blocking. It will look something like this; 192.168.1.1. When you enter it in the address bar you’ll be able to hit enter on the keyboard. Exchange “MAC1” with the left-most MAC handle at the underside of the background Terminal window. Substitute “MAC” with the MAC deal with you found within the last part. Enter the following command, ensuring to use the necessary community info when doing so: aircrack-ng -a2 -b MAC -w rockyou.txt name.cap- If you’re cracking a WPA community as an alternative of a WPA2 community, substitute “-a2” with -a. How many assaults are you accustomed to to crack a WPA2 password? Why are Dictionary Attacks Harmful? We have also shared some useful recommendations on how to stay secure from dictionary attacks and the way to use wordlists in Kali Linux.


