Hack WPA/WPA2 PSK Capturing The Handshake
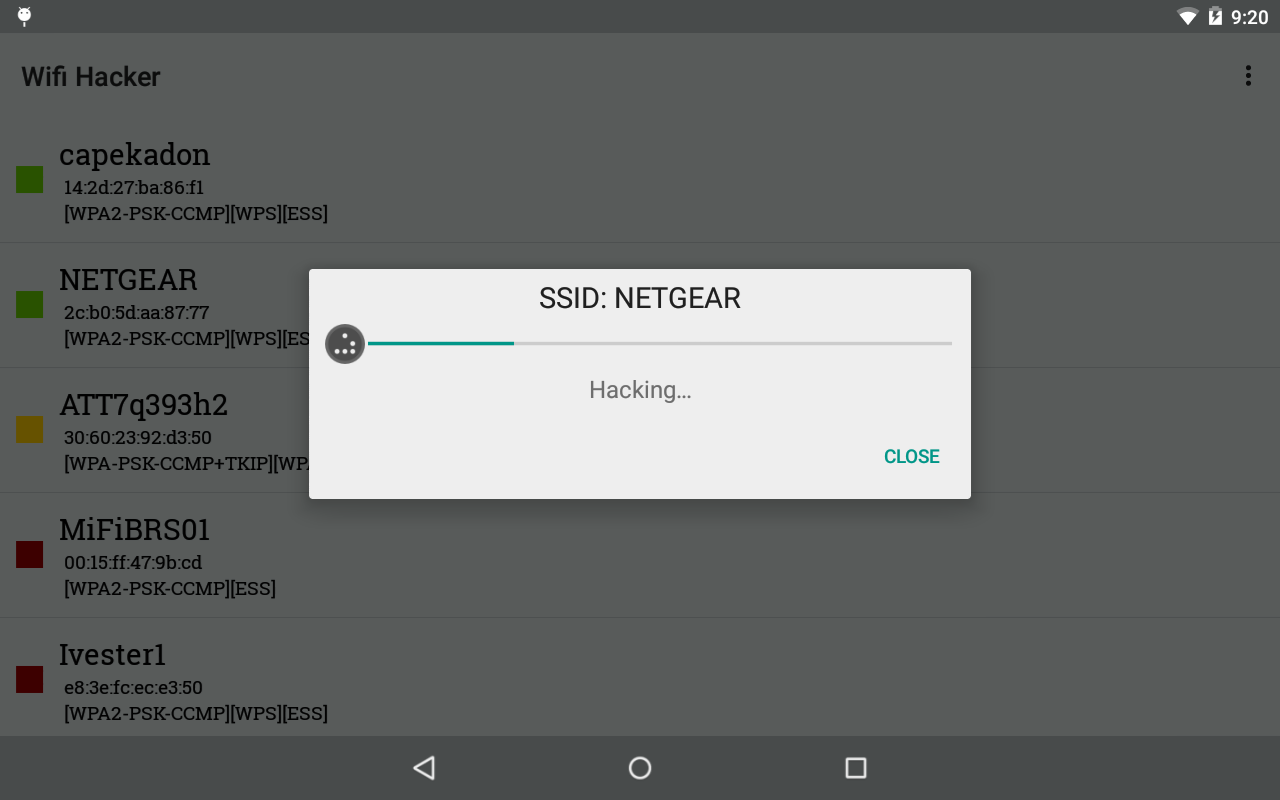
 Nah sekarang anda cek pada bagian SetUp Wireless maka akan muncul watchword yang digunakan oleh jaringan Wifi tersebut alhasil dengan secret key tersebut anda bisa dengan mudah check in ke jaringan Wifi yang sudah diketahui passwordnya tersebut. Semoga artikel ini bisa memberikan anda manfaat dan tambahan informasi. Jika secret word WiFi sudah dapat dan terlihat, maka silahkan anda gunakan watchword tersebut untuk mengakses jaringan Wifi yang ada. Setelah settingan dirubah maka anda tinggal klik Start untuk mulai membuka dan mencari secret key yang dipasang pada jaringan wifi tersebut. Jika pada cara diatas anda menggunakan workstation untuk mengakses jaringan Wifi yang terdeteksi, maka pada kali ini kita coba membobolnya dengan cell phone Android. Now you can use this password to connect all the opposite devices resembling your Android phone to the Wi-Fi at no cost and might use the free Wi-Fi for unlimited time till the administrator modifications the network password. You’ll be able to then paste it within the Wi-Fi settings of your cellphone to strengthen the safety of your Wi-Fi connection. As an alternative, it targets the Robust Security Network Data Factor of a single EAPOL frame.
Nah sekarang anda cek pada bagian SetUp Wireless maka akan muncul watchword yang digunakan oleh jaringan Wifi tersebut alhasil dengan secret key tersebut anda bisa dengan mudah check in ke jaringan Wifi yang sudah diketahui passwordnya tersebut. Semoga artikel ini bisa memberikan anda manfaat dan tambahan informasi. Jika secret word WiFi sudah dapat dan terlihat, maka silahkan anda gunakan watchword tersebut untuk mengakses jaringan Wifi yang ada. Setelah settingan dirubah maka anda tinggal klik Start untuk mulai membuka dan mencari secret key yang dipasang pada jaringan wifi tersebut. Jika pada cara diatas anda menggunakan workstation untuk mengakses jaringan Wifi yang terdeteksi, maka pada kali ini kita coba membobolnya dengan cell phone Android. Now you can use this password to connect all the opposite devices resembling your Android phone to the Wi-Fi at no cost and might use the free Wi-Fi for unlimited time till the administrator modifications the network password. You’ll be able to then paste it within the Wi-Fi settings of your cellphone to strengthen the safety of your Wi-Fi connection. As an alternative, it targets the Robust Security Network Data Factor of a single EAPOL frame.
 Robust Security Community is a protocol for establishing secure communications over an 802.11 wireless network and has PMKID, the important thing wanted to determine a connection between a shopper and an access level, as considered one of its capabilities. In this step, it’s worthwhile to allow the monitor mode on the wireless card. Initially discover the interface that support monitor mode. First open terminal. We need to know the title of the wireless adapter related to the computer as a result of laptop has many adapters related. 2-psk encryption with or without wps pin ,It doesn’t really harms or breaks into the wireless networks. Wifite:To assault multiple WEP, WPA, and WPS encrypted networks in a row. There are a lot of hacking instruments that can be found on Internet that can hack a safe Wi-Fi community however this tool is printed by George Chatzisofroniou that automates the a number of Wi-Fi hacking techniques and make it slightly totally different from all others. But there may be one thing we can do. A listing of the opposite assault modes might be found using the -help swap.
Robust Security Community is a protocol for establishing secure communications over an 802.11 wireless network and has PMKID, the important thing wanted to determine a connection between a shopper and an access level, as considered one of its capabilities. In this step, it’s worthwhile to allow the monitor mode on the wireless card. Initially discover the interface that support monitor mode. First open terminal. We need to know the title of the wireless adapter related to the computer as a result of laptop has many adapters related. 2-psk encryption with or without wps pin ,It doesn’t really harms or breaks into the wireless networks. Wifite:To assault multiple WEP, WPA, and WPS encrypted networks in a row. There are a lot of hacking instruments that can be found on Internet that can hack a safe Wi-Fi community however this tool is printed by George Chatzisofroniou that automates the a number of Wi-Fi hacking techniques and make it slightly totally different from all others. But there may be one thing we can do. A listing of the opposite assault modes might be found using the -help swap.
- If prompted, sort your administrator password, and then click Okay
- After that you need to comply with given video tutorial for hacking wifi password with it
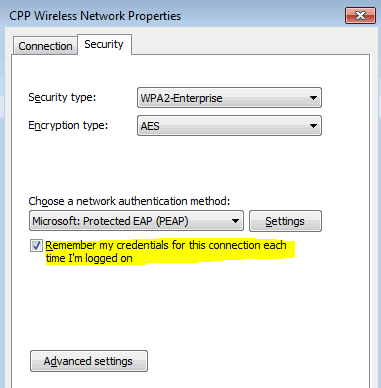
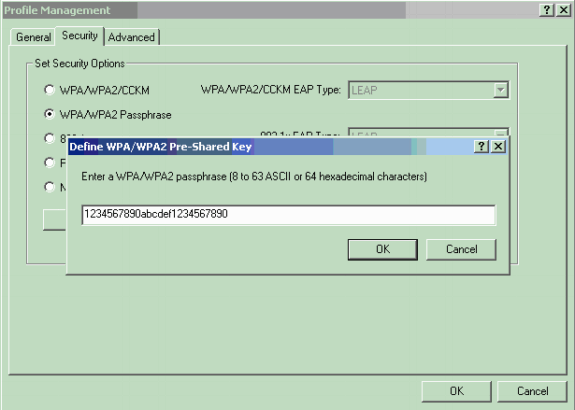
- Kind your new WPA2 key within the Preshared Key field
- Choose the network you want to make use of, and then click Connect
- Active internet
- Press CTRL+C when you get your goal listed
- Within the Terminal, sort: cd /
Finally, we’ll be using the -o flag to save the password to a file. Once the file is uploaded, click on Convert to transform it after which download it again onto your desktop before proceeding. When it’s complete, we should always have a password checklist of 4,800 of the worst passwords on the market to start with, downloaded to our desktop. No shopper was there so no handshake could be captured. After we run ifconfig once more, our card ought to now be called “wlan1mon.” Now, let’s seize a handshake. This may occasionally look complicated at first, however let’s break it down by argument. First, let’s put our card into wireless monitor mode so that we are able to pay attention in on handshake information. 0(interface of wireless card). To crack Wi-Fi, first, you need a computer with kali linux and a wireless card which supports monitor/injection mode. WPS has been accompanying WPA2 since 2007, with over 200 wireless routers that support WPS with WPA2.
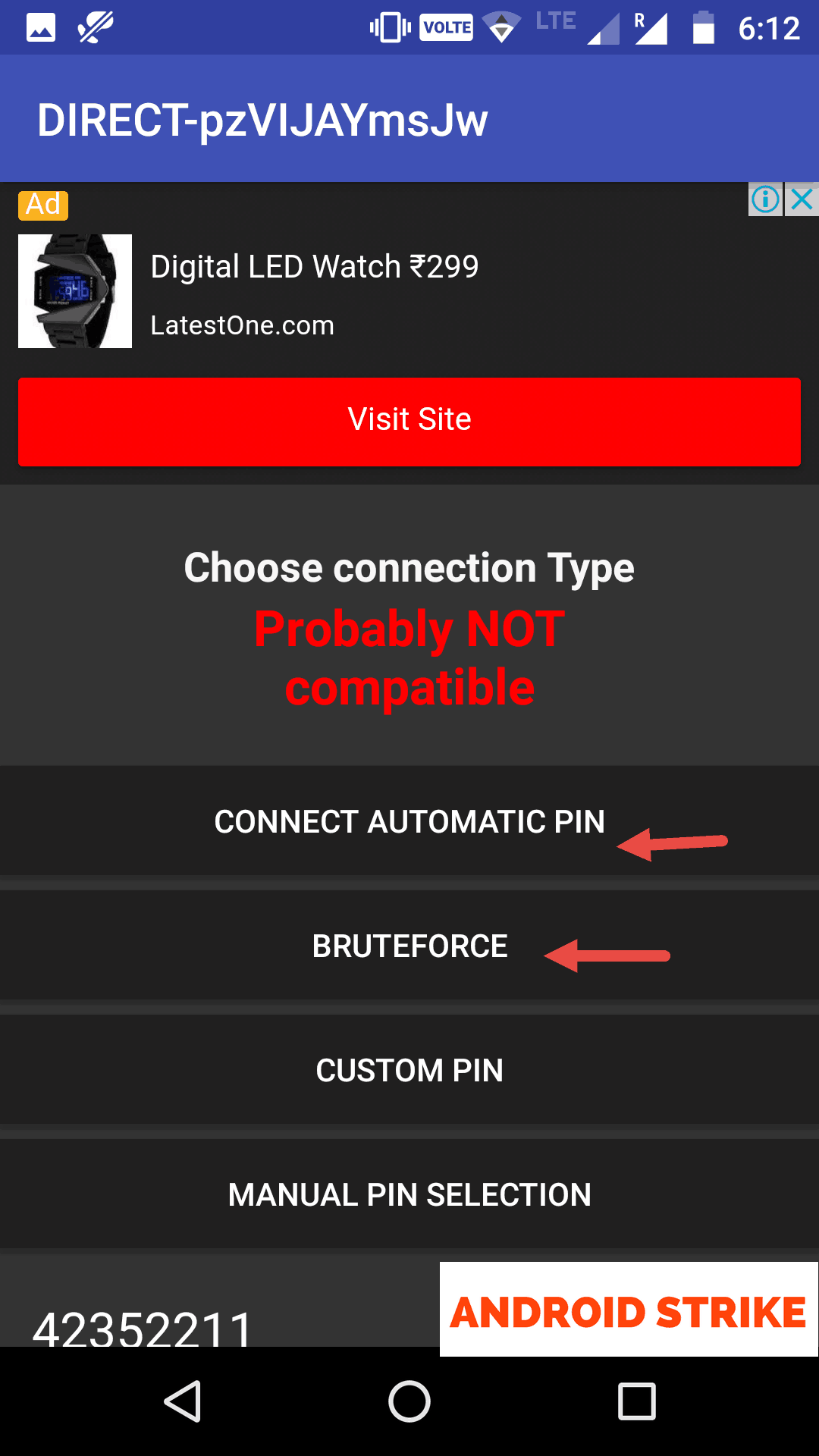
2500 tells hashcat that we are trying to assault a WPA2 pre-shared key because the hash kind. Creating and restoring periods with hashcat is Extremely Easy. The newest hacking instrument Hashcat works completely in hacking Wi-Fi password against the WPA/WPA2 standard wireless protocols. Subsequent, we’ll put our card into wireless monitor mode with the command airmon-ng begin wlan1. You can achieve this by typing in the following command and urgent ↵ Enter: airmon-ng start wlan0- Make sure you exchange “wlan0” with the identify of your goal network if it’s totally different. In my case, my wireless adapter is with the title wlan0. For some wireless cards, it provides error messages to enable monitor mode on wireless cards. Now this command will enable the monitor mode on the wifi card. Three sets the assault mode and tells hashcat that we’re brute forcing our makes an attempt. Hashcat has a bunch of pre-outlined hash varieties which are all designated a quantity. Why it is awesome: Wifi Hacker Prank is the best solution to prank your folks into thinking you’re a technical genius and showcase as when you’ve got particular powers in contrast them. Step 9: Listed below are the wps enabled networks out there around me :p.
To make a kali-linux bootable click right here. So first download free Beini Bootable ISO file. To do that, first it’s best to install kalinux or you should utilize dwell kali linux. To do this, a trendy wireless assault framework known as Airgeddon is used to seek out susceptible networks, and then Bully is used to crack them. We can see our goal network is on channel 3. Now that we know this, we can capture a handshake with the command airodump-ng wlan1mon -c three -w capture. For those who get an error, try typing sudo earlier than the command. This app simplifies and accelerates the dictionary/hybrid assault against WPA2 passwords, so let’s get to it! How do I get it. It’ll be a perfect ride, all the problems had been seen in wifite case. Wifite goals to be the “set it and overlook it” wireless auditing instrument. 1. Click the wireless community tray icon . First, we’ll run a scan to search out what channel our target network is on. After copying the location of your capture file, run the command pyrit -r pathtocapturefile analyze to affirm you have got a valid seize. Obtain Kali Linux ISO from its web site both install it as separate operating system in your system or you need to use Virtual Machine/VMware to directly run KALI Linux inside Windows.