The Difference Between WEP, WPA, And WPA2 Wi-Fi Passwords

Even when you understand you could secure your Wi-Fi community (and have already achieved so), you most likely discover all the safety protocol acronyms a bit of bit puzzling. What does it matter what the little acronym subsequent to the safety protocol you chose was? This Method found during the assault towards the not too long ago released WPA3 safety commonplace which is extraordinarily tougher to crack since its used Simultaneous Authentication of Equals (SAE), a fashionable key establishment protocol. Enter the variety of which Wi-Fi you want to crack. Due to this fact, if you’d like a simple means out with out indulging in the otherwise unethical act of hacking/cracking wireless community passwords then merely convert your Computer right into a hotspot wherever you are. Most of the fashionable routers are secured from all types of attacks. “At this time, we have no idea for which distributors or for what number of routers this system will work, but we predict it’ll work towards all 802.11i/p/q/r networks with roaming capabilities enabled (most modern routers),” Steube added.
As soon as the user logs again in, you will be provided with a handshake. Search for a handshake. Your inputted command ought to exactly appear to be this. If you’re purchasing for a new router, search for one which supports the newest security customary called WPA3. A flaw in a function added to Wi-Fi, referred to as Wi-Fi Protected Setup (WPS), permits WPA and WPA2 safety to be bypassed and successfully broken in many situations. We see the new file called yyyyy-bbbbb.txt. If any person is already linked to the network, you can test in his community properties to see what encryption-sort is being using by the focused WiFi network. We’ll use hcxpcaptool to convert our PCAPNG file into one Hashcat can work with, leaving solely the step of choosing a strong record of passwords in your brute-forcing attempts.It’s value mentioning that not each network is weak to this assault. Rename your “.cap” file. Convert the “.cap” file into “.hccapx” format. After getting sufficient knowledge in the file bell-01.cap, run the command aircrack-ng bell-01.cap.
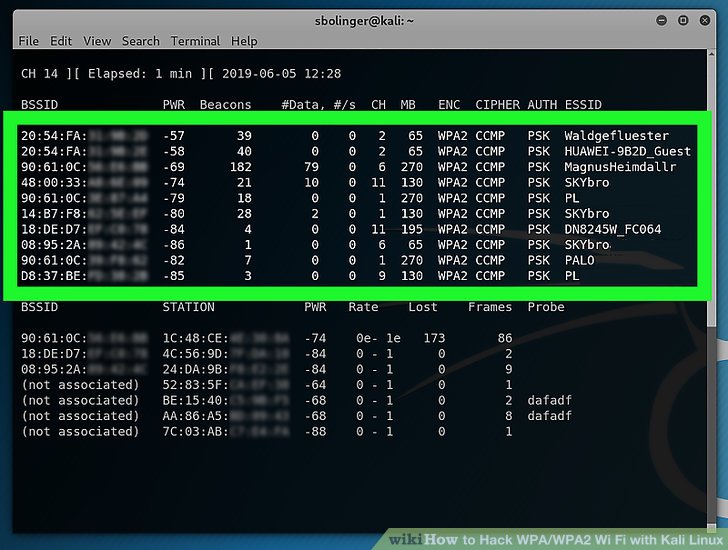
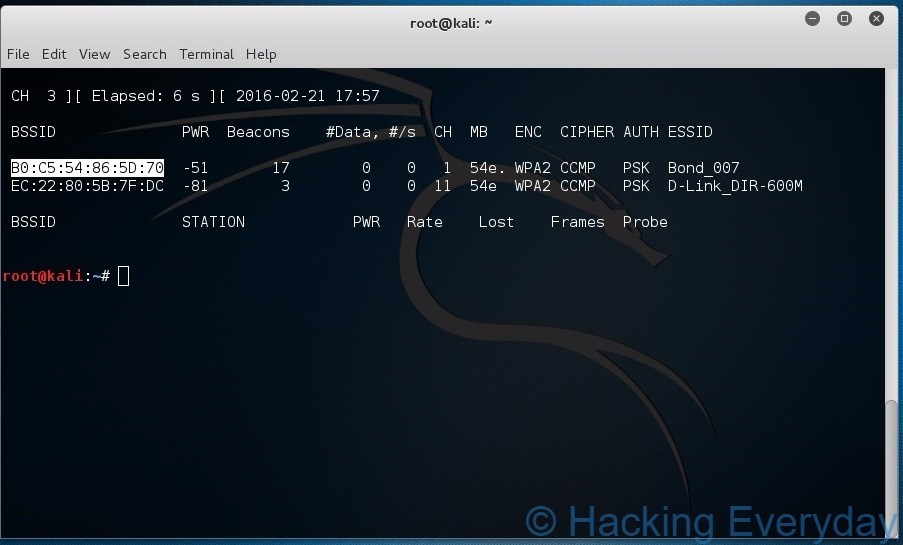
Enter the next code, ensuring to substitute the required components of the command along with your network’s data: airodump-ng -c channel —bssid MAC -w /root/Desktop/ mon0- Change “channel” with the channel quantity you found within the last step. Ensure that airodump-ng is still operating within the background Terminal window. T to open the Terminal. Exit airodump-ng, then open the desktop. A brand new method has been found to simply retrieve the Pairwise Grasp Key Identifier (PMKID) from a router utilizing WPA/WPA2 security, which may then be used to crack the wireless password of the router. A wireless router is a networking system that permits a person to arrange a wireless connection to the Web. Anyone within the WiFi vary can connect his device to the network without any password in take pleasure in free web. 7 Which Wordlist and Password checklist are you using in Kali Linux? These items of data are to the left of the network’s name:MAC address — This is the line of numbers on the far-left facet of your router’s line.
- The generated faux wpa2 wpa key or wps pin and it is going to be displayed
- We’ll use interface WLAN1 that supports monitor mode
- The AP doesn’t use WPS
- Kali Linux OS
- Right-click on the title of your wireless network, and then click Standing
- Click scan and anticipate 30second. Then select the wifi that have shopper as shown in under
- Next Matter
- You will be requested to decide on Back Observe three or 4, similar to picture below
PMK Title”, the entry point’s MAC handle and the station’s MAC tackle.” acknowledged Steube’s publish on this new method. Here, -c 1 indicates channel quantity which is 1, -w bell is to write down information in file “bell”, -bssid 64:0F:28:6B:A9:B1 is MAC deal with for my chosen WiFi entry level and mon0 is monitor interface that was created above. Change “MAC2” with the proper-most MAC tackle at the bottom of the background Terminal window. Change “MAC1” with the left-most MAC deal with at the underside of the background Terminal window. Open terminal in Kali Linux and enter the command airmon-ng. Open your Kali Linux computer’s Terminal. Re-open the unique Terminal window. Before we proceed further, we need know what a part of WPA/WPA2 is actually susceptible. Yes, potentially… we are still at an excessive amount of time to crack with just one AMI, we want many AMI machines to attach all together and create a distributed service.
To help beef up your router’s safety, here are five ways for defending your house community, gadgets and files from hackers. That allows you to do the same hacking as the hackers do. I used to be in a position to connect my printer to the identical router hardware on its guest community utilizing a WPA2 password without areas. You possibly can see within the picture below that Hashcat has saved the session with the same title i.e blabla and operating. You’ll see the password displayed in brackets to the precise of the “KEY Discovered! As soon as you’re completed with this step, you may proceed with hacking your chosen community.- If you’ve already arrange the card in your pc before, you’ll nonetheless need to set it up for Kali Linux right here by plugging it in. You’ll find this in the “Interface” column.- If you’re hacking your personal community, it can normally be named “wlan0”. The target can be to make use of a Kali-compatible wireless community adapter to seize the data needed from the network to try brute-forcing the password. Kind in the password you employ to log into your pc, then press ↵ Enter.