How One Can Hack: Cracking Wifi Passwords With Cowpatty (WPA2)
This new wifi hacking technique was accidentally discovered by Jens Steube lead developer in well-liked password-cracking instrument Hashcat while he was analyzing the newly-launched. The team behind password-cracking software Hashcat have hit on a fresh technique to reccover wireless network credentials faster and with out the need for somebody to log onto a target network. Because of that, you should be very cautious when downloading programs off the web that relate to password cracking of WiFi networks. Cracking other individuals WiFi is prohibited and towards law. Also, if you’re apprehensive about “wardrivers” or folks roaming round in search of Wi-Fi spots to hack, you’ll be able to disable the broadcasting of your community and your guest network’s name (SSID) entirely. However, as a result of the nature of this wireless community technology, there are methods around the security and other people can truly crack the password. 7. Hack any network security. No wifi network is 100% safe,some could be cracked in as little as a minute others take a bit longer. Securing a house community will not be always straightforward – even when you take all of the precautions you possibly can.
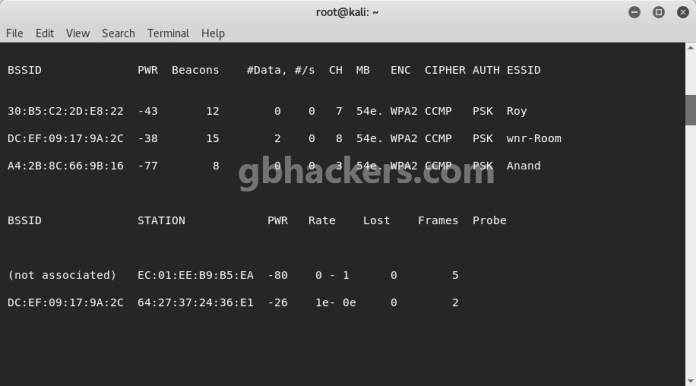
All we have to do is find a WiFi hotspot nearby our residence or public place and just use the software program for looking out and retrieving its password. Place the Kali Linux ISO file on the flash drive. First Run hcxdumptool to realize the PMKID from the AP and dump the file in PCAP format utilizing the next code. It’s then after these requests that the access point dispatch the primary EAPOL frame which comprises the PMKID in RSN layer. Attempt the default password file first and if it’s not profitable, advance to a larger, more full password file resembling one of those. The appliance will attempt to connect with WPS enabled Wifi Routers that have the WPS vulnerability using some algorithms to connect with the Wifi. Because of this, purchasers will attempt to reestablish the connection at which point airodump-ng will seize and save all handshake activities. You will save a lot of time conserving that in mind. This can start a dump on the selected AP (00:25:9C:97:4F:48), on the selected channel (-c 9) and save the the hash in a file named cowcrack. Its not a traditional .txt file so I am unsure, or might i simply change it into a txt file and be high-quality?
- Wireless card (help promiscuous mode)
- Wireless Router
- To make use of the .cap in the hashcat first we will convert the file to the .hccapx file
- Provides details of all of the access points that are available

We’ll add it by adding the -r flag, with the location of the file containing our handshake immediately after. Search for a handshake. The place you wrote it down as a result of you already know you’d overlook so you will have a log e book for all your passwords, pin numbers, key values, and many others. Simply pull the e book out and look it up. On this tutorial from our Wi-Fi Hacking collection, we’ll take a look at utilizing aircrack-ng and a dictionary attack on the encrypted password after grabbing it in the 4-approach handshake. The final step can be to crack the captured handshake using a password dictionary. Analyzes wireless networks and if the network password is the default one using encryption WEP -WPA and WPA2, you may pretend hacking wifi community safe. Ans: Yes, it really works, but not on all sorts of networks and routers. Ans: Same reply as above, as a result of it is not programmed to hack superior routers. Since the brand new WiFi hack only works against networks with roaming functions enabled and requires attackers to brute drive the password, customers are really useful to guard their WiFi network with a secure password that’s difficult to crack. It takes follow. What worked for me is hack my very own router until I bought good at it.
The attack will be executed using a virtualized occasion of Kali Linux on VMware using an EdiMax wireless adaptor and a TP-Link wireless router. It’s now time to build a quantity list of eight digits long utilizing Crunch. If the cracking was run with the complete potential of the hardware, software program and assist of additional GPU’s, the cracking time can significantly reduce. As shown in Figure 7 by populating the parameter Aircrack-ng will start cracking the password. If we begin a benchmark check on Linux AMI we can see soon the difference. Ken Munro, a director at Pen Test Partners, advised The Each day Swig that the sensible utility of the attack in the real world will be configuration-dependent. You may at all times change the password generated by the app. A stolen password permits an adversary to abuse someone else’s web connection, as an illustration compromising the firewall, making a fraudulent transaction or performing different criminal activities.