HACK WPA/WPA2-PSK With Out BRUTEFORCE Utilizing FLUXION

PSK uses a Key Outlined by the Network Administrator. Except the Administrator decides to alter it. An excellent tactic is to place visitor units on a separate network. Stations are the Computer systems/Smart Phones or any Wireless Units currently linked to the BSSID they are Associated with. Open up a Konsole and sort in “iwconfig” to see your Wireless Interfaces. To obtain , sort the following right into a terminal window. 5. Now sort “spoonwep” and enter. Additionally, I hope you could have googled by now to see in case your Wireless Card will support Packet Injection or not. As you can see in the above Image, My Wireless Card Reveals up as “wlan0”. If you’ve an intention aside from ‘fun’ & ‘learning’, you’ll be able to cease studying now. Now that we are Prepared.. Our Wireless Interface “mon0” will now capture Packets only from Channel 1 from a specific BSSID and write all the info to a File referred to as “wep.ivs”.

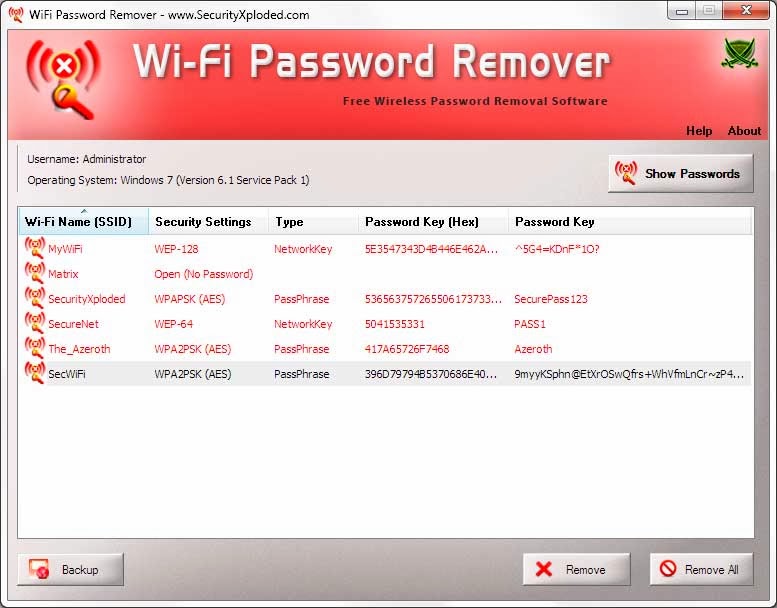
Data: Number of captured data packets (if WEP, distinctive IV count), together with data broadcast packets. Every submitted password is verified by the handshake captured earlier. Dictionary hack uses the dictionary for hacking the password, it tries all the mix of phrases obtainable in dictionary and if the password is mixture of dictionary words, then this method is the best technique to hack any password. It is another greatest Wi-Fi hacking tools that let the customers crack WPA protected Wireless networks. MiniDWEP GTK hacking password methodology. A Dictionary that has the Password we are attempting to get. There are some particulars in there too. Before we Scan for WPA/WPA2 Networks, There may be something I need to make a note of here. Following WiFite section was taken from a previous guide Cracking Wifi WPA2 WPA passwords using pyrit cowpatty in Kali Linux which was among the best guides about cracking Wifi passwords on the market. Hashcat or oclHashcat or Hashcat on Kali Linux bought built-in capabilities to attack and decrypt or Cracking WPA2 WPA with Hashcat – handshake .cap files. Cracking WPA2 WPA with Hashcat in Kali Linux (BruteForce MASK primarily based attack on Wifi passwords) new !
- Wihack Crack Wireless
- [e]xit utterly
- 00:19:5B:52:Advert:F7 00:1C:BF:90:5B:A3 -29 0- 1 12 four TestNet
- It will close automatically – after getting the right password
I’ve created a particular MASK file to make issues sooner. So lets say you password is 12345678. You need to use a custom MASK like ? Lets Configure the airodump-ng command to focus Particularly on The Goal Network. So, Lets De-Authenticate the Consumer and Get the Handshake. Its an Authentication Course of to permit the Shopper to be related to the Access Level. But at least you don’t must batch process this way. As I’ve let you know that Its an ISO format that may be burned into CD/USB pen drive/flash drive for making Bootable reside-CD or Pin Drive. Chipsets that supported wireless card are the leading AR9271 chips, Ralink, Atheros, and so forth. So obtain free Beini ISO is a LiveCD/USB operating system. Surf Web FREE By UNLOCKING WPA/WPA2 WIFI NETWORKS Passkeys! What you’re Seeing is An inventory of All the WPA/WPA2 Encrypted WIFI Networks around you. With powerfully software program and WiFi adapter you’ll be able to audit WiFi access factors.
12. Supported all kinds of Wifi Adapter and Land Card. WiFi hack software is simple to use. This is the only Method ever to hack a wpa/wpa2 – wps networks. On this post I will let you know tips on how to crack wpa/wpa2 wi-fi in kali linux utilizing aircrack-ng. TKIP makes use of a Ever Changing Key which makes it Usesless to Crack. Neck of all of it, It’s ineffective to crack a TKIP Authenticated WPA/WPA2. TKIP – Temporal Key Integrity Protocol. Hence, The important thing remains the identical. PSK – Pre Shared Key. This Tutorial will solely enable you to crack PSK Authenticated WPA/WPA2. Whereas Stations are not essential to crack a WEP Encrypted Community, Stations are a must need to crack a WPA/WPA2 Protected Network. At any time when, a Shopper connects to a WPA/WPA2 Encrypted Network, It exchanges a “4-approach Handshake” with the AP. This guide is aimed to help you crack WPA/WPA2 Passwords.. This video will make it easier to in packet capture. You possibly can ask them within the comments field under – I’ll attempt that will help you out.
We at present don’t know how many suppliers or what number of routers this technique can use on merchandise, however we predict it’s going to work with 802.11i / p / q / r networks that allow community switching. It’s crucial to use something extra powerful, but shopping for a brand new graphics card shouldn’t be a proper solution. Right click on and duplicate the name of the monitor interface. Now, We are going to put the Wireless Card into Monitor Mode. When the Screen Hundreds, Enter “startx” to move on to Graphical Mode. Q. After i boot from the Disc, I can’t see the Icons on the underside of the screen. Purchasers may reconnect too quick so that you can see that they had been disconnected. That is what it might appear to be in case your Wireless Interface is Successfully put into Monitor Mode. In this Mode, Quite Merely, We will likely be in a position to watch all the Traffic that flows around in our Scan Area. So, We’ll go ahead and Scan the area.